I have many friends who are libertarians, and when I spew here regarding politics I often hear from them in…
There is shockingly little truth in any of the normal outlets in America. Universities, mainstream media, common conversation — they…
I’ve been coming repeatedly to a simple conclusion regarding content creation and the use of social services: If something is…
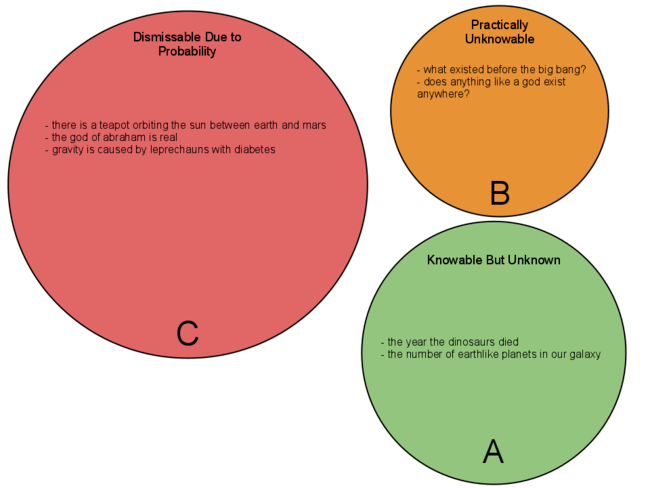
Many are confused about the meaning of agnosticism as it relates to things we as humans are not certain about….
Microsoft has warned organizations worldwide that threat actors are ramping up their exploitation of critical vulnerabilities in on-premises Exchange Server…
From StackOverflow: You mention cutting with yy and complain that you almost never want to cut whole lines. In fact…
At BSides-LasVegas this year I saw an exemplary talk on the history of lock technology and lock picking. Not only…
One of the most commonly held debates between non-believers is that of whether someone is agnostic or atheist. The problem…
The horse is dead. Design, feel, features, openness, customizability — we’ve heard it all. The main arguments are well understood…
My web configuration makes use of Varnish as a front-end, and I noticed a bug recently where asking for “/study”…
Nation-state cyber threats have evolved dramatically over the past decade, with attackers employing increasingly sophisticated persistence techniques to maintain long-term…
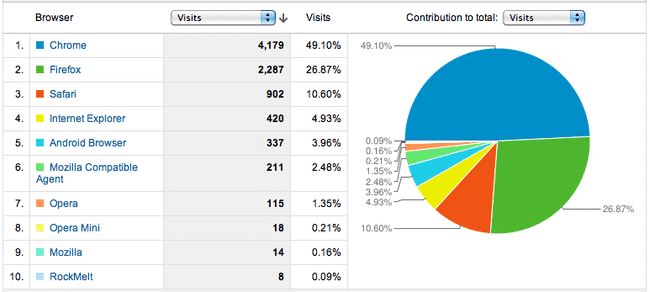
I spent yesterday on the front page of Hacker News for my git primer, which resulted in over 12K page…