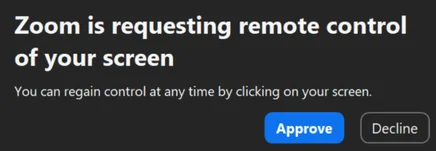
Did you know that when participating in a Zoom call, you can grant permission to other participants to control your…
If you frequent Hacker News and Reddit as I do you’re probably familiar with a certain type of rant regarding…
Cybercriminals lure content creators with promises of cutting-edge AI wizardry, only to attempt to steal their data or hijack their…
These days, hackers don’t break in — they log in. Using valid credentials, cybercriminals bypass security systems while appearing legitimate…
In today’s hyper-connected world, cybersecurity is no longer the sole responsibility of a dedicated security team. As organizations scale and…
Microsoft has reported significant strides in thwarting financial fraud across its ecosystem. From April 2024 to April 2025, the tech…
I love my job This isn’t said sarcastically or trying to convince myself. I genuinely love my job. I love…
If you use Burp a good bit you’ve likely run into the question of what precisely the various Intruder Payload…
A newly discovered vulnerability, CVE-2024-53141, in the Linux kernel’s IP sets framework has exposed a critical security flaw that allows…
The traditional “castle-and-moat” model of cybersecurity is outdated. Firewalls, endpoint protection and segmentation are all still important. But if you…
Cybersecurity Ventures recently asked AI “Why use YouTube for marketing?” and it replied “YouTube is a powerful marketing tool because…
A new multi-stage attack has been observed delivering malware families like Agent Tesla variants, Remcos RAT, and XLoader. “Attackers increasingly…