High-profile cyberattacks involving ransomware, malware, zero-day exploits, and nation-state intrusions dominate headlines. These attacks are bold, disruptive, and external, commanding…
I’ve been stupid for Astaro since the early 00’s and I remain so today. Today I run it in a…
Data breaches are no occasional crisis – they are a persistent, costly epidemic wreaking global havoc on businesses. While organizations…
Here’s a look at the most interesting products from the past week, featuring releases from Cato Networks, Cyware, Entrust, PlexTrac,…
It’s highly annoying when you are trying to read or download something at a client site only to be denied…
An e-commerce industry leader has suggested that Hong Kong allow a popular quick payment operator to arbitrate online transactions amid…
In this Help Net Security interview, Dr. Dag Flachet, co-founder at Codific, explains what the Cyber Resilience Act (CRA) means…
Many believe the discussion of free will is pointless. This is usually because one believes it’s been settled (for the…
Should we negotiate? Should we pay? These are the questions every organization faces when cybercriminals lock their data. By the…
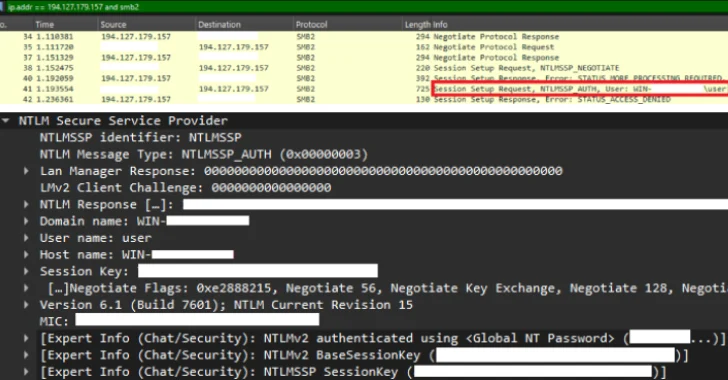
Apr 18, 2025Ravie LakshmananWindows Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a medium-severity…
Many are confused by the terms decompiler and disassembler. As with most confusion of this type, most just use the…
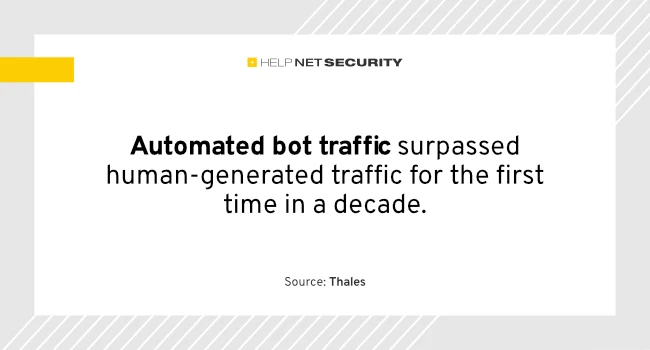
Rise in accessible AI tools significantly lowered the barrier to entry for cyber attackers, enabling them to create and deploy…