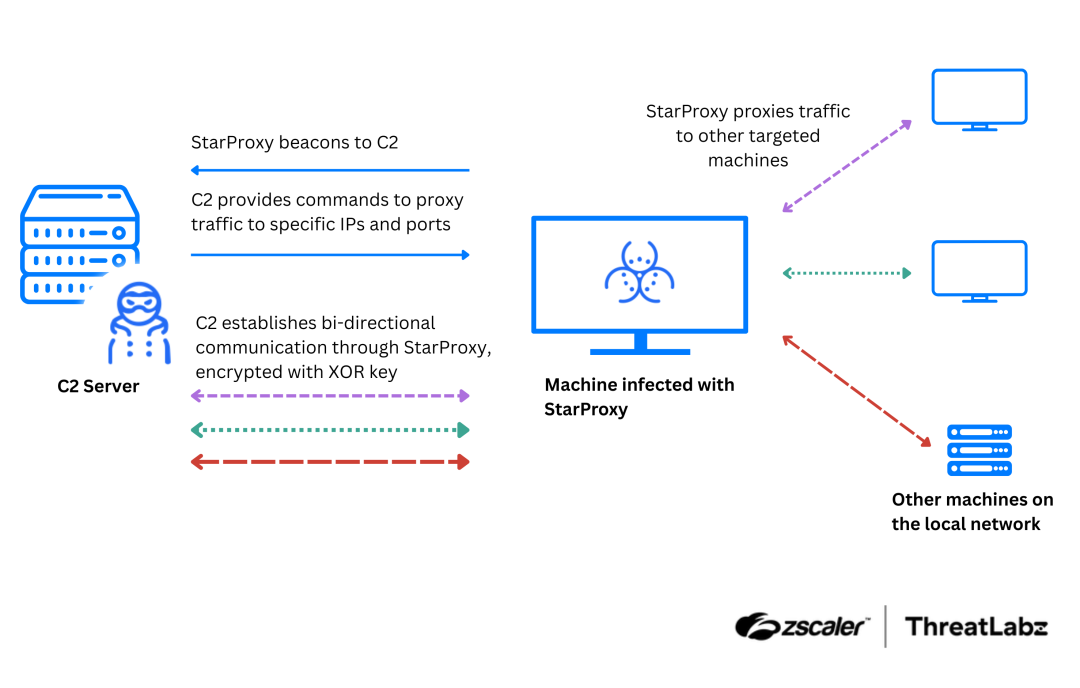
A comprehensive study by zLabs, the research team at Zimperium, has found that over 43% of the top 100 mobile…
I recently attended a company blogging conference call where the topic was how to properly categorize and tag posts for…
A critical vulnerability in the Erlang/OTP SSH, tracked as CVE-2025-32433, has been disclosed that allows for unauthenticated remote code execution on…
The 12th Edition of the Microsoft Vulnerabilities Report has revealed a significant surge in the number of vulnerabilities detected within…
Following reports of unauthorized access to a legacy Oracle cloud environment, CISA warns of potential credential compromise leading to phishing,…
China-linked APT Mustang Panda upgrades tools in its arsenal Pierluigi Paganini April 17, 2025 China-linked APT group Mustang Panda deployed…
For those who use Ubuntu or Debian and still use apt-get and apt-cache search, you might want to start thinking…
Entertainment venue management firm Legends International warns it suffered a data breach in November 2024, which has impacted employees and…
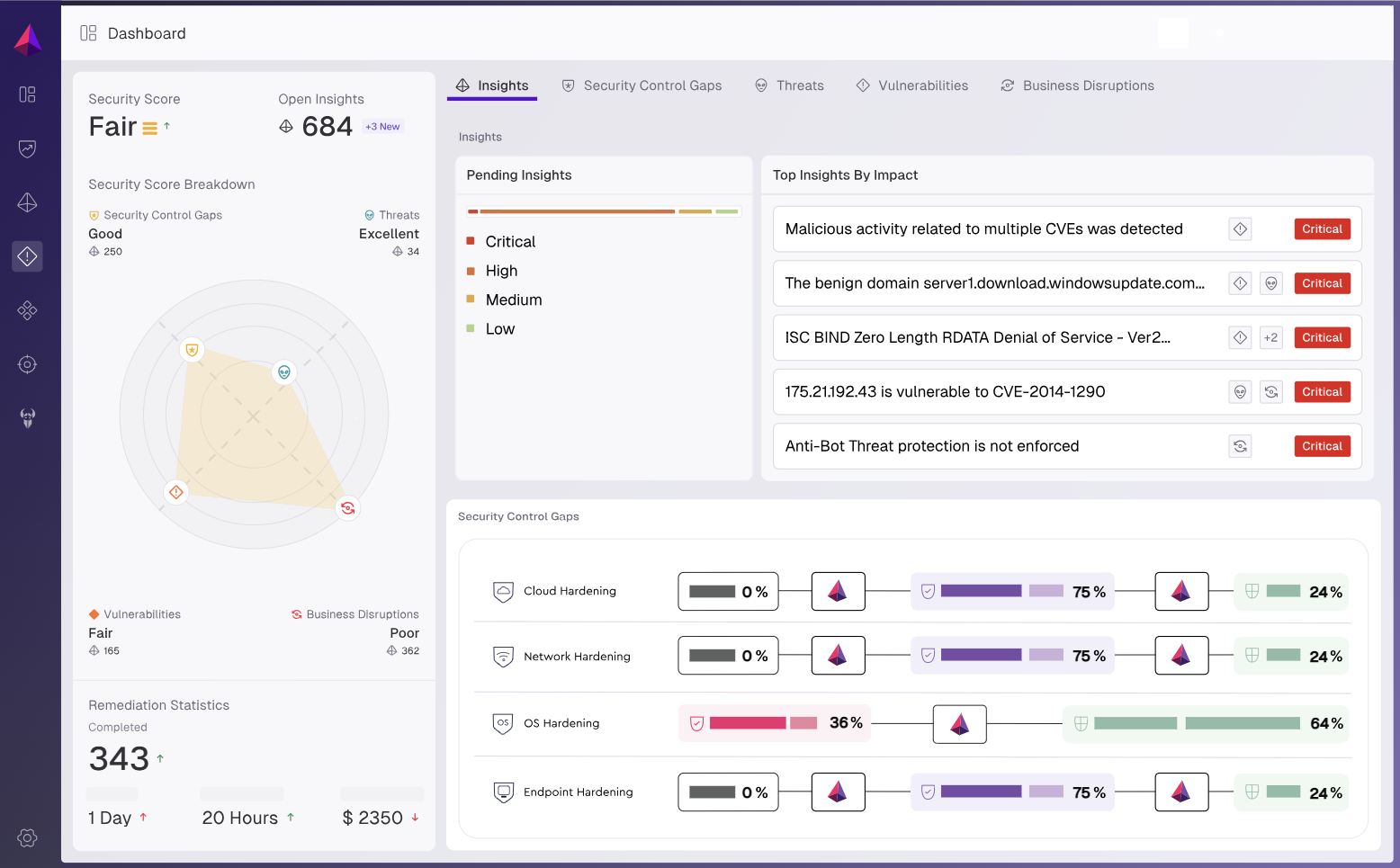
By Gary S. Miliefsky, Publisher, Cyber Defense Magazine Transforming Exposure Management with Safe, Automated Remediation Organizations today invest heavily in…
A sophisticated multi-layered phishing campaign was uncovered, employing a complex attack chain known as “Cascading Shadows” to deliver various malware,…
We’re all well aware of the growing list of high-quality universities offering free online classes. It’s remarkable by any measure….
A relatively new ransomware outfit known as CrazyHunter has emerged as a significant threat, particularly targeting Taiwanese organizations. The group,…