This is an attempt to show the differences–not without bias, but without hate. Functionality The iPhone focuses on doing a…
Google has announced the removal of 5.5 billion malicious advertisements and the suspension of over 700,000 offending advertiser accounts in…
Zoom, the widely popular video conferencing platform used by millions of IT professionals, educators, and businesses worldwide, has recently experienced…
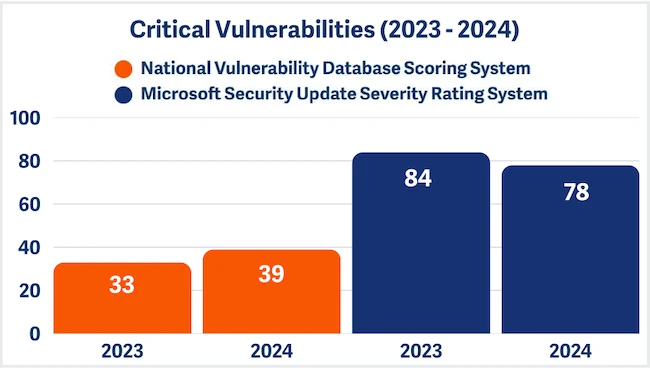
Microsoft reported a record 1,360 vulnerabilities in 2024, according to the latest BeyondTrust Microsoft Vulnerabilities Report. The volume marks an…
Apr 17, 2025Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a security…
I believe that humans transferring their minds to digital form is inevitable. In fact, I think it’s precisely the way…
Cisco has disclosed a high-severity vulnerability in its widely used Webex App, warning users that attackers could exploit the flaw…
In this Help Net Security interview, Jason Lord, CTO at AutoRABIT, discusses the cybersecurity risks posed by AI agents integrated…
My feelings as a Christian points me to my Lord and Savior as a fighter. It points me to the…
I posted here an absolutely brilliant and terrifying political cartoon. It’s about the way in which America (the West?) will…
Hands-On Industrial Internet of Things is a practical guide designed specifically for professionals building and securing industrial IoT (IIoT) systems….
Apr 17, 2025Ravie LakshmananZero-Day / Vulnerability Apple on Wednesday released security updates for iOS, iPadOS, macOS Sequoia, tvOS, and visionOS…