Something about realtime web analytics is just cool to me. I think it’s the idea of visualizing the interactions with…
Email security solutions are critical for protecting organizations from the growing sophistication of cyber threats targeting email communication. As email…
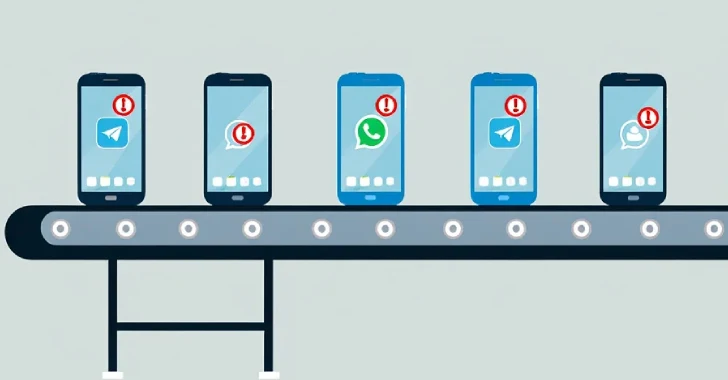
Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that…
Government contractor Conduent disclosed a data breach Pierluigi Paganini April 16, 2025 The business services provider Conduent told the SEC…
CapitalizationWriting the first letter of a word in uppercase, and the rest of the letters in lowercase. Title CaseAll words…
In today’s rapidly evolving cybersecurity landscape, incident response teams are increasingly advocating for unified logging standards to effectively combat security…
Security Operations Centers (SOCs) are facing a mounting crisis: alert fatigue. As cyber threats multiply and security tools proliferate, SOC…
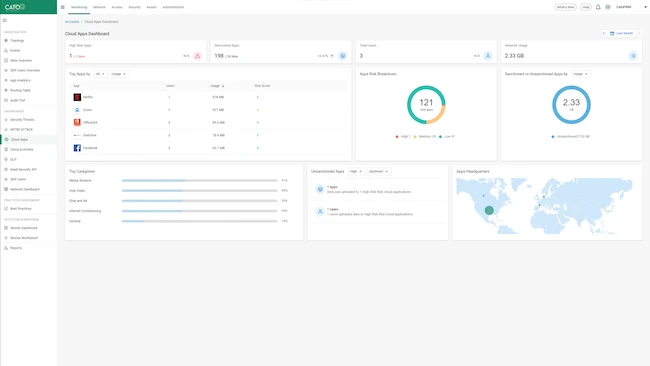
Cato Networks introduced GenAI security controls for Cato CASB (Cloud Access Security Broker). Cato CASB, a native feature in the Cato SASE…
By Associate Professor Dr. Sheeba Armoogum, University of Mauritius In 2025, the paradigms of human hacking are undergoing a substantial…
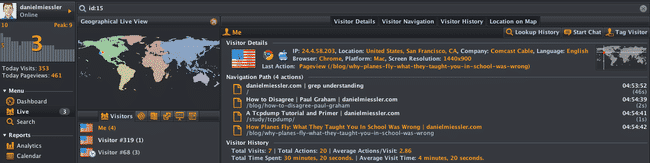
Jun 4, 2010 I’ve written before about how SocialTech’s main purpose is to present each of us as an API,…
Law enforcement agencies across Europe and Türkiye have successfully dismantled four major encrypted communication platforms used extensively by criminal networks. …
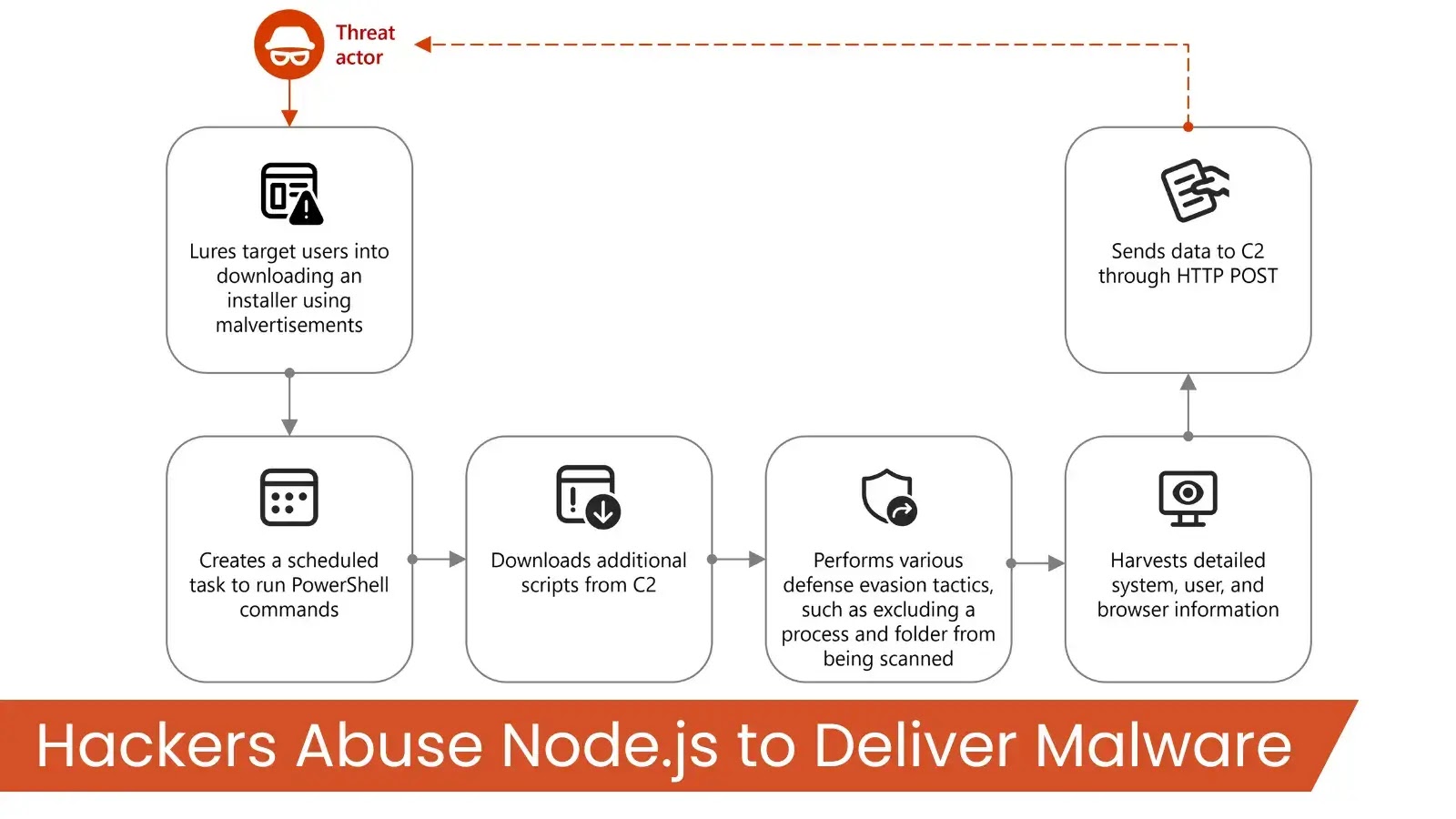
Threat actors are increasingly targeting Node.js—a staple tool for modern web developers—to launch sophisticated malware campaigns aimed at data theft…