Security Operations Centers (SOCs) are facing a mounting crisis: alert fatigue. As cyber threats multiply and security tools proliferate, SOC…
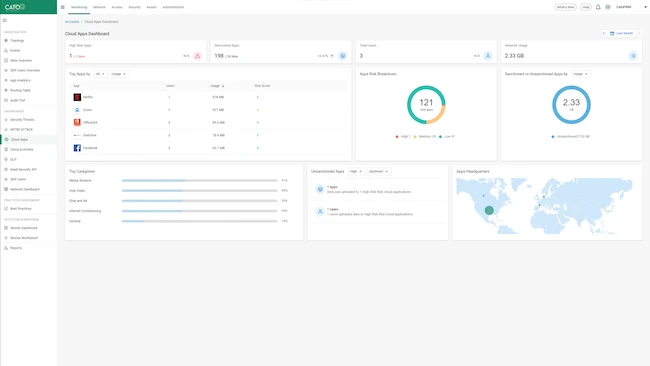
Cato Networks introduced GenAI security controls for Cato CASB (Cloud Access Security Broker). Cato CASB, a native feature in the Cato SASE…
By Associate Professor Dr. Sheeba Armoogum, University of Mauritius In 2025, the paradigms of human hacking are undergoing a substantial…
Jun 4, 2010 I’ve written before about how SocialTech’s main purpose is to present each of us as an API,…
Law enforcement agencies across Europe and Türkiye have successfully dismantled four major encrypted communication platforms used extensively by criminal networks. …
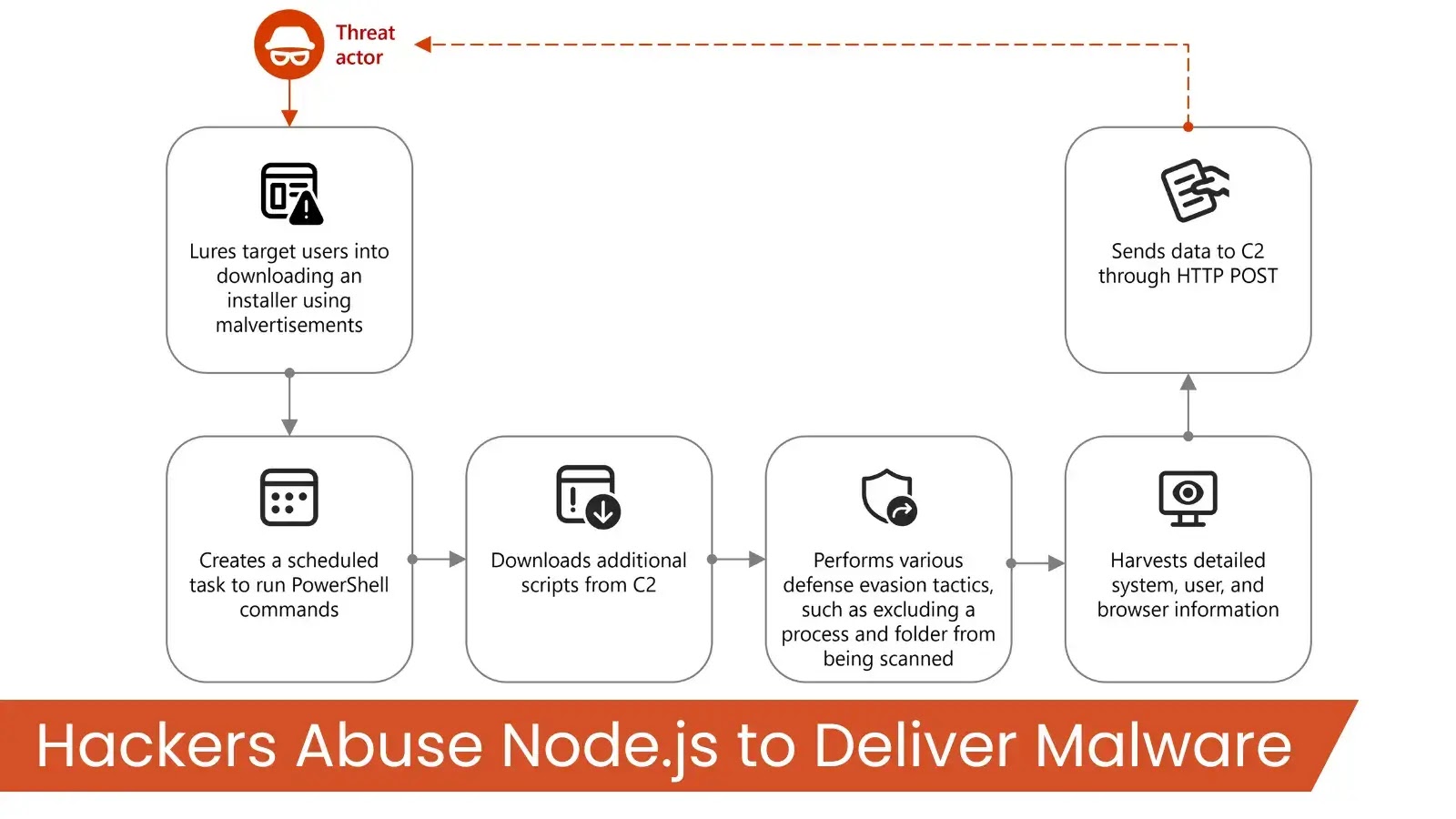
Threat actors are increasingly targeting Node.js—a staple tool for modern web developers—to launch sophisticated malware campaigns aimed at data theft…
Ideas suck. Ideas are everywhere and pop into our heads all of the time. Ideas are not the inspirational spark…
MITRE Vice President Yosry Barsoum has warned that U.S. government funding for the Common Vulnerabilities and Exposures (CVE) and Common…
A critical vulnerability in Windows 11 allowed attackers to escalate from a low-privileged user to full system administrator rights in…
A leaked internal memo dated April 15, 2025, has sent shockwaves through the cybersecurity community, revealing that MITRE’s contract to…
In an era where data drives strategy and personalized outreach is key to consumer engagement, marketing teams face mounting pressure…
For CISOs, mergers and acquisitions (M&A) bring both potential and risk. These deals can drive growth, but they also open…