Apr 16, 2025Ravie LakshmananVulnerability Management / Incident Response The U.S. government funding for non-profit research giant MITRE to operate and…
While reading certain publications recently I’ve been paying a bit more attention to the typography and capitalization. The main thing…
Advanced Persistent Threats (APTs) represent some of the most sophisticated cyber threats organizations face today. Unlike conventional attacks, APTs involve…
Zeek, formerly known as Bro, has established itself as a leading open-source network security monitoring platform. As organizations face increasingly…
Despite being present on virtually every employee’s browser, extensions are rarely monitored by security teams or controlled by IT, according…
So I just implemented memcached. It’s basically a system that uses hash tables to serve content directly from memory rather…
Ever feel like phishing scams are on a never-ending quest for supreme deception? From fake delivery notifications to impersonated CEOs,…
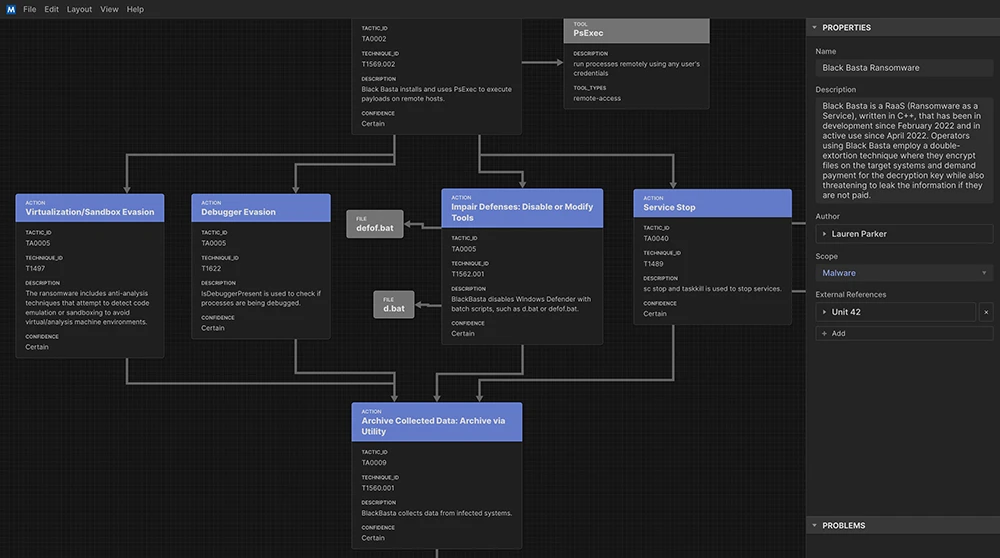
MITRE’s Attack Flow project aims to translate complex cyber operations into a structured language. By describing how adversaries sequence and…
My buddies and I are doing a Harn campaign right now and one of the mechanics involves accruing stat “checks”…
A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware…
By now, most CISOs agree: passwords are the weakest link in the authentication chain. They’re easy to guess, hard to…
Image from scientificamerican.com Scientists are now discovering that self-control is a precious, finite resource that can be raised and lowered…