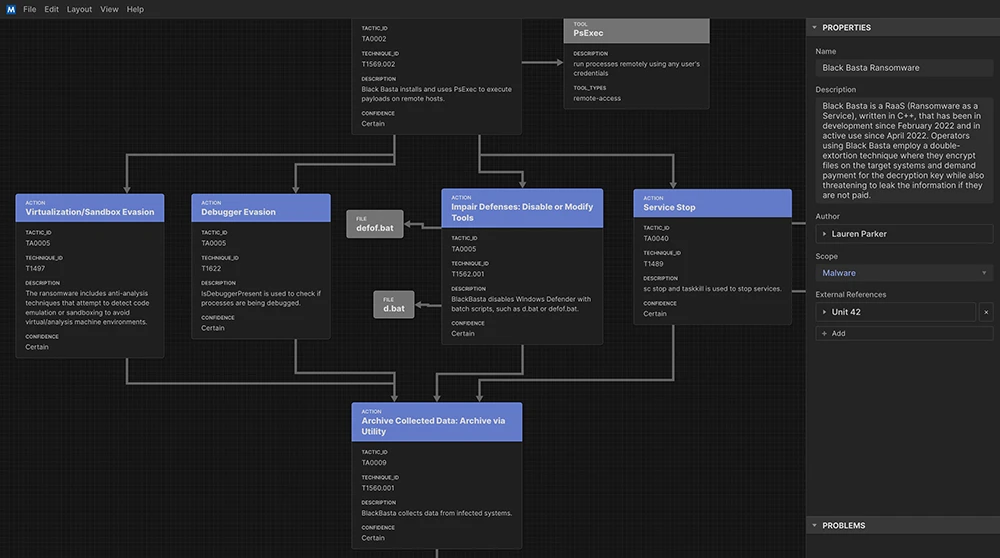
MITRE’s Attack Flow project aims to translate complex cyber operations into a structured language. By describing how adversaries sequence and…
My buddies and I are doing a Harn campaign right now and one of the mechanics involves accruing stat “checks”…
A critical resource that cybersecurity professionals worldwide rely on to identify, mitigate and fix security vulnerabilities in software and hardware…
By now, most CISOs agree: passwords are the weakest link in the authentication chain. They’re easy to guess, hard to…
Image from scientificamerican.com Scientists are now discovering that self-control is a precious, finite resource that can be raised and lowered…
I am an enthusiastic user of the Verisign PIP two-factor authentication service. It’s a system that allows you to add additional…
First, watch the talk. Believe me–it’s worth it. Now, I think the talk is brilliant, and I think he makes…
Google has issued an urgent security update for its Chrome browser after two critical vulnerabilities were discovered. These vulnerabilities could…
So perhaps you’ve heard the story of evil America trying to enact a draconian immigration policy towards Mexico. It’s the…
[ NOTE: This is an older configuration, and my latest can be found here. ] If you are into blogging…
The only way to have a real discussion is to realize that both parties think they are doing good, and…
Keeping up with crypto tax laws in Europe feels like a constant hurdle. Regulations evolve, tax authorities demand precise reporting,…