Russian state-sponsored espionage group Midnight Blizzard is behind a new spear-phishing campaign targeting diplomatic entities in Europe, including embassies. Midnight…
A letter from MITRE, dated April 15, 2025, has leaked online claimed to be revealed from a reliable source that…
4chan is down amid claims from a rival Soyjak forum user who says they’ve breached the site and leaked its…
People often wonder what others think of them. If you use Twitter to any significant degree there’s a simple way…
Microsoft 365 administrators faced significant challenges today as an ongoing outage prevented access to the Microsoft 365 Admin Center and…
The anonymous image board 4chan has survived years of controversy. It weathered user and advertiser boycotts as well as damning…
A new and highly sophisticated ransomware campaign, dubbed “DOGE BIG BALLS Ransomware,” has recently come to light, demonstrating a blend…
Both can be bypassed by smart attackers who know they’re being profiled. Both have moderate success in catching less-dedicated attackers….
Landmark Admin has issued an update to its investigation of a cyberattack it suffered in May 2024, increasing the number…
For many years, ransomware has been associated with online extortion, causing businesses to become immobilized as they attempt to recover…
Cybercriminals have launched a sophisticated campaign targeting websites hosted on Amazon Web Services (AWS) EC2 instances. This campaign, observed in…
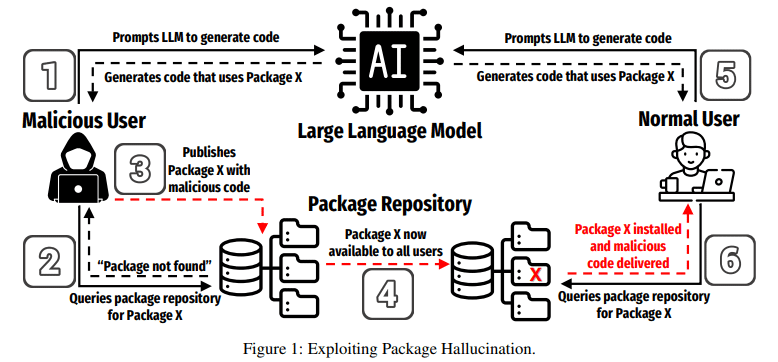
Code-generating large language models (LLMs) have introduced a new security issue into software development: Code package hallucinations. Package hallucinations occur…