Hertz Corp. confirmed a threat actor gained access to sensitive personal data in a breach linked to vulnerabilities in Cleo…
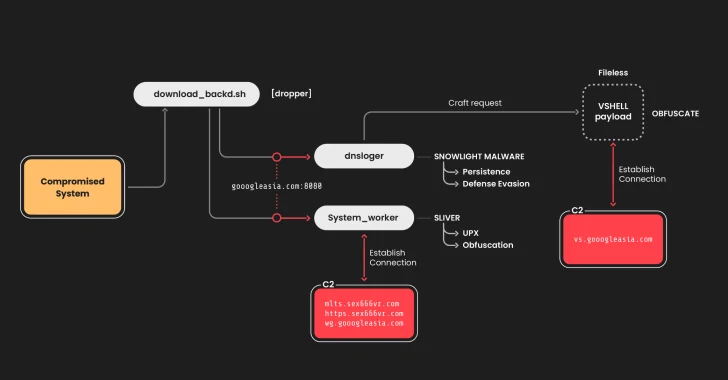
A Chinese state-sponsored hacking group has been observed using recently released open-source offensive security tools and other tactics in an…
Microsoft warned that Exchange 2016 and Exchange 2019 will reach the end of support six months from now, on October…
A seemingly empty folder appearing on Windows systems after recent security updates has raised concerns among users, but Microsoft confirms…
We’ve spent months analyzing how AI-powered coding assistants like GitHub Copilot handle security risks. The results? Disturbing. The Hidden Risks…
Security researchers have unveiled a new malware process injection technique dubbed “Waiting Thread Hijacking” (WTH), designed to execute malicious code…
Following a number of recent high-profile events, edge and border defence technologies such as firewalls, VPN gateways and intrusion prevention…
American car rental company Hertz has suffered a data breach linked to last year’s exploitation of Cleo zero-day vulnerabilities by…
The Hertz Corporation, on behalf of Hertz, Dollar, and Thrifty brands, is sending breach notifications to customers who may have…
Apr 15, 2025Ravie LakshmananLinux / Malware The China-linked threat actor known as UNC5174 has been attributed to a new campaign…
Car hire giant Hertz has disclosed a worldwide data breach affecting the UK and other major markets, after becoming embroiled…
Critical Apache Roller flaw allows to retain unauthorized access even after a password change Pierluigi Paganini April 15, 2025 A…