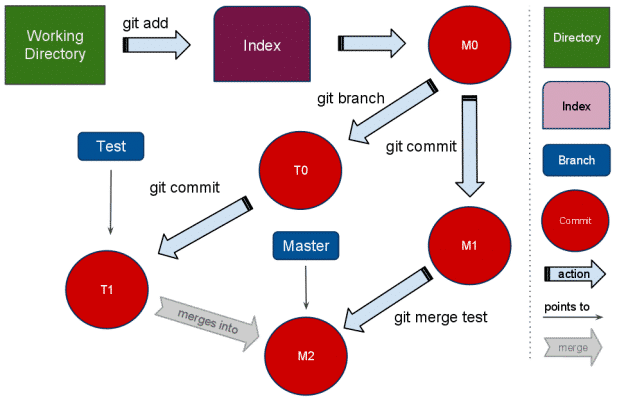
Sometimes when you first install git you realize you added a bunch of crap to your repository, which makes it…
A new sophisticated attack campaign where cybercriminals are exploiting Microsoft Teams to deliver malware and maintain persistent access to corporate…
Across the globe, a new kind of threat is targeting the very institutions dedicated to shaping the future: schools, colleges,…
The Rise of Zero-Click Spyware Recent revelations about a zero-click exploit targeting WhatsApp users underscore the growing threat of sophisticated…
Organizations are fixing less than half of all exploitable vulnerabilities, with just 21% of GenAI app flaws being resolved, according…
Conservatives long for the world of Leave it to Beaver, Christmas Story, and Babe Ruth. A world of everyone looking…
In today’s interconnected business environment, organizations increasingly rely on third-party vendors, suppliers, and partners to deliver critical services and functions….
Early-stage startups face unique cybersecurity challenges that established enterprises have already addressed through years of investment and experience. For Chief…
CISO Department of Justice | Australia | On-site – View job details As a CISO, you will be responsible for…
I see the cloud as a means by which business units will disentangle themselves from internal IT shops, eventually moving…
Car rental giant Hertz says Australians’ data “may” have been exposed in a breach of a file transfer platform used…
Here are three related scenarios: You own the DVD of a good movie, but you never watch it. But if…