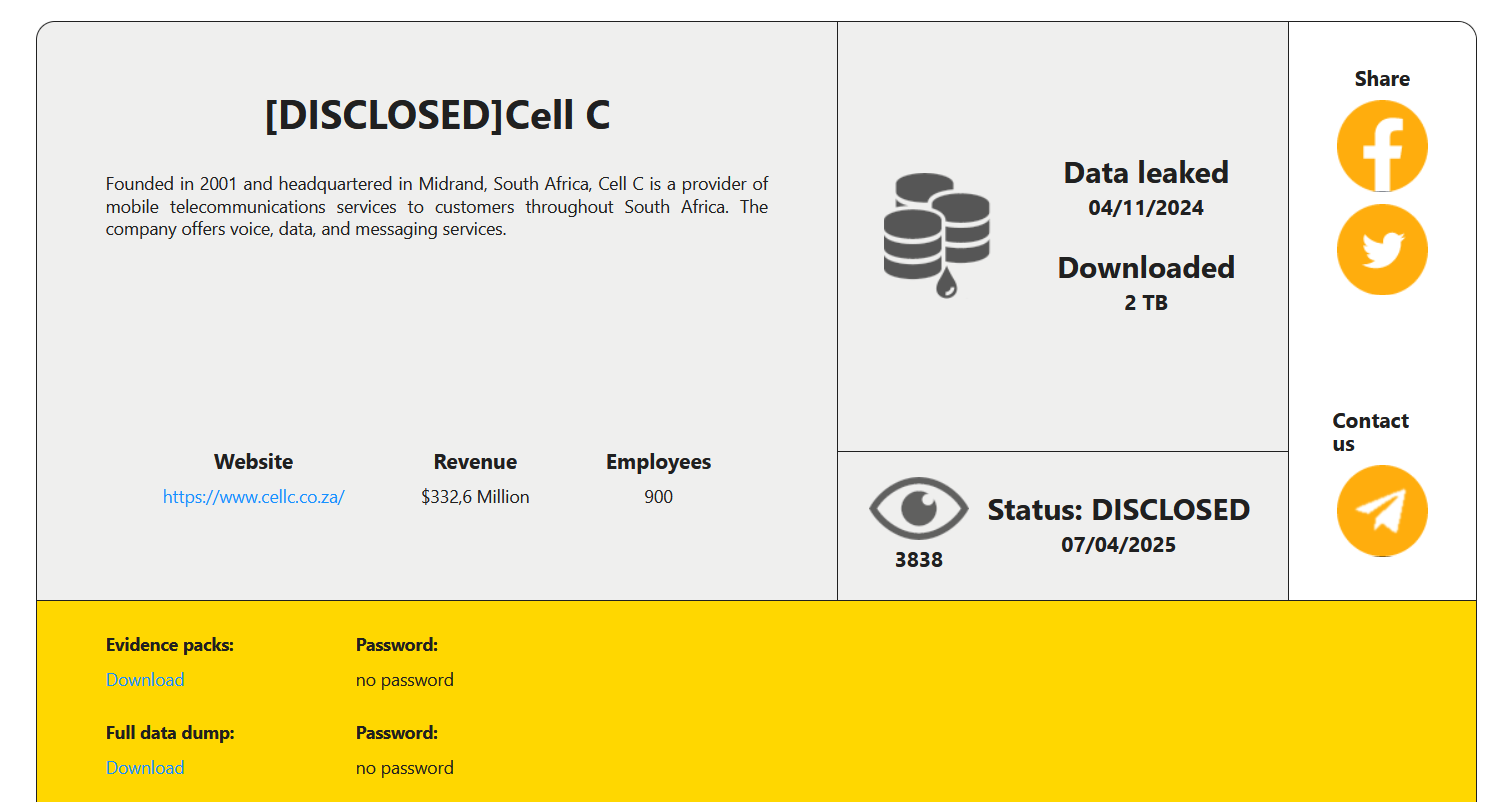
South African telecom provider Cell C disclosed a data breach following a cyberattack Pierluigi Paganini April 14, 2025 Cell C,…
The code below does the following: Read a list of IPs Send each line (IP) to the ipinfodb web service…
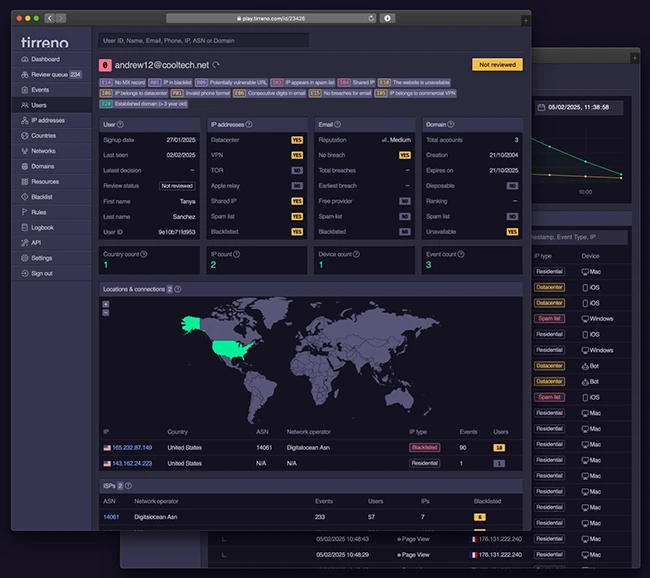
Tirreno is an open-source fraud prevention platform designed as a universal analytics tool to monitor online platforms, web applications, SaaS…
Prospa, an online lender for small business, has used hackathons and graph database technology to map out complex relationships between…
This is an interesting post about how the concept of PageRank for URLs is becoming dated at best, and obsolete…
In recent years, we’ve witnessed a range of cyberattacks targeting critical infrastructure and both public and private sector entities. These…
As AI becomes embedded in daily business workflows, the risk of data exposure increases. Prompt leaks are not rare exceptions….
Compromised passwords, unpatched vulnerabilities and unauthorised applications can all lead to an endpoint being exploited by threat actors. Peter Soulsby,…
One of the advantages of social content sharing is that if I like what you write then there’s a good…
In today’s digital age, personal and professional data are constantly being stored, transferred, and backed up across various devices. Among…
Data breaches are rising across industries, hitting healthcare, finance, and retail especially hard. The damage goes beyond lost data, as…
One thing that bothers me severely is the concept of a conditional friendship. There are a few ways these come…