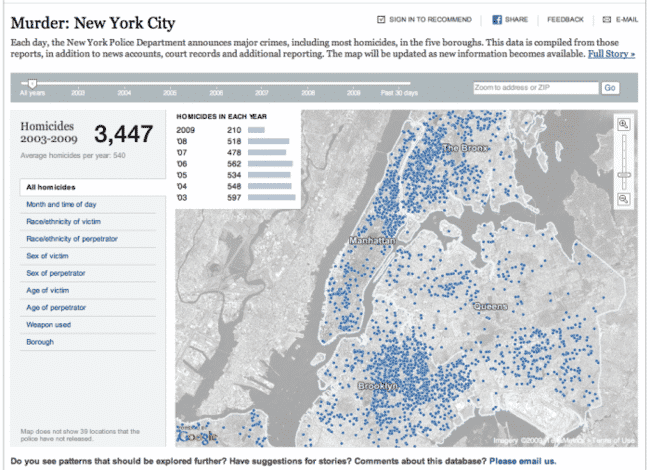
Few things get me as excited as data visualization. I seriously love the stuff, and this project by the New…
Cloud security company Zscaler has released its ThreatLabz 2025 VPN Risk Report, commissioned by Cybersecurity Insiders. The report highlights the…
Here’s how to redirect from one domain to another within Apache using .htacess. This is how to do it permanently…
An investigation by Fortinet has uncovered a post-exploitation technique used by a threat actor. During this investigation, a threat actor…
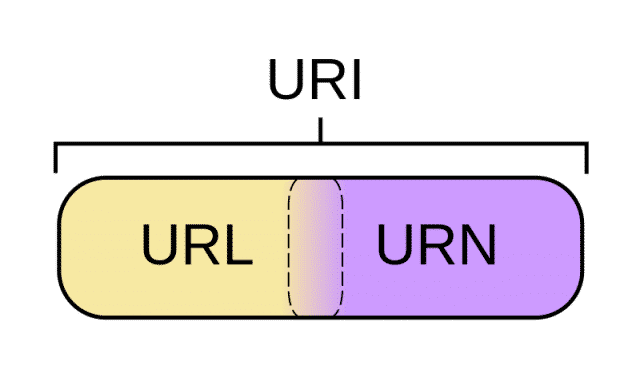
So I have an idea for a project. The idea is to document the core concepts taught in the major…
Identity security company CyberArk has released a first-of-its-kind machine identity security solution, the Secure Workload Access Solution. The company says…
So I finally accomplished something with the site I’ve been wanting to do for a couple of months now–my “Discovered…
The Hong Kong Monetary Authority (HKMA) will announce on Monday new measures to be implemented by banks to safeguard the…
I think my argument for feel vs. features has been thoroughly supported over the last few years of iPhone success….
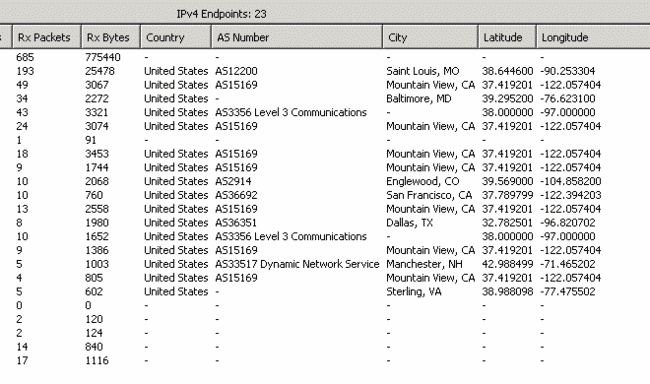
Laura Chappell just posted a great tutorial on getting GeoIP working with the new version of Wireshark (1.2). I set…
What follows is a primer on the key security-oriented characteristics of the HTTP protocol. It’s a collection of a number…
As of the last year or so my preferred method for installing and updating nmap is to use subversion. It’s…