Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Overview of the PlayPraetor Masquerading Party Variants CTM360 has now identified a much larger extent of the ongoing Play Praetor…
An APT group exploited ESET flaw to execute malware Pierluigi Paganini April 10, 2025 At least one APT group has…
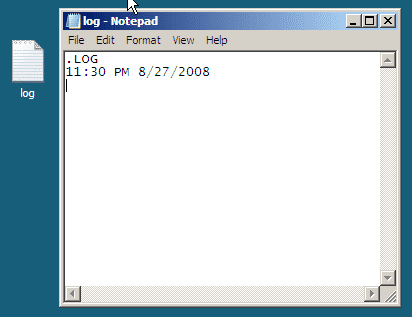
Yeah, that Notepad. It has a feature that few know about, and I’m not talking about word wrap. You can…
Security awareness training doesn’t have to be a snoozefest – games and stories can help instill ‘sticky’ habits that will…
A sophisticated malware campaign dubbed “HollowQuill” has emerged as a significant threat to academic institutions and government agencies worldwide. The…
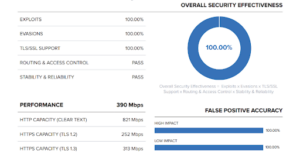
Organisations demand uncompromising protection against today’s most pressing threats while ensuring minimal disruption to legitimate business operations. Check Point CloudGuard…
A hacker operating under the alias “Satanic” has claimed responsibility for a massive data breach involving WooCommerce, a leading e-commerce…
Law enforcement authorities have announced that they tracked down the customers of the SmokeLoader malware and detained at least five…
Many, especially in the blogsphere, are fond of saying, “This country is becoming fascist.” Or, “We’re on a path to…
Every year, the number of vulnerabilities discovered and recorded increases. The sheer volume of vulnerabilities makes it impractical for organizations…
Here’s how to avoid being hit by fraudulent websites that scammers can catapult directly to the top of your search…