Facebook has officially launched ThreatExchange – a collaborative social network where companies can share information on cybersecurity threats, in an…
A significant denial-of-service vulnerability (CVE-2025-0128) is affecting multiple versions of their PAN-OS firewall software. The flaw allows unauthenticated attackers to…
Ever wanted to take a piece of WordPress functionality and put it in a non-WordPress portion of your website? Like,…
With Valentine’s Day nearly upon us, millions will be looking for love online. Here’s six online dating scams to look…
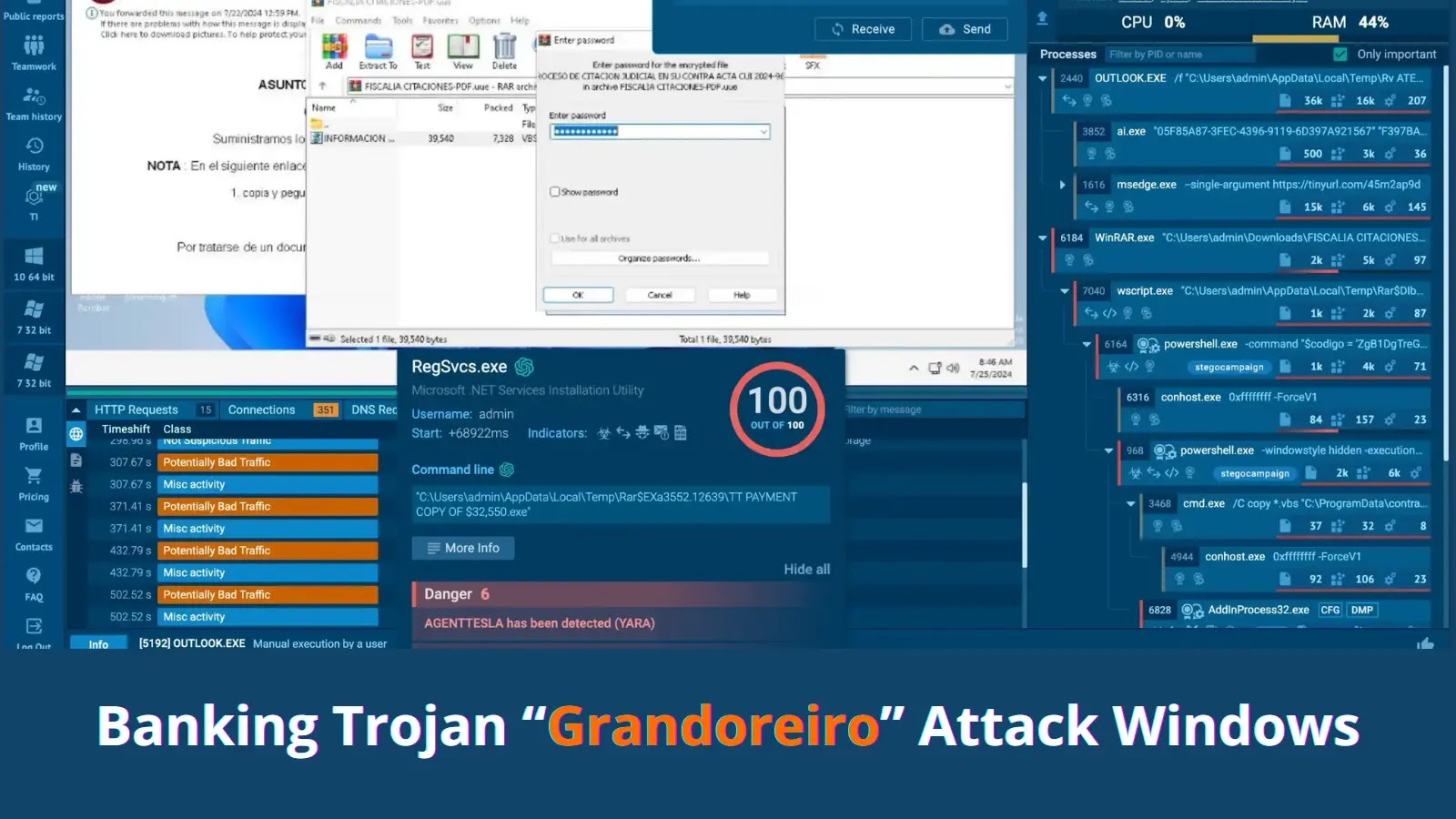
A new wave of phishing emails is sweeping across Latin America, and once again, Grandoreiro is behind it. This banking…
For years, global cybersecurity alerts have been issued to safeguard a variety of devices—ranging from personal computers and smartphones to…
From a psychological standpoint, we all crave attention, and likes and comments fuel that need, encouraging us to share even…
7-Eleven Australia’s general manager of strategy and technology, Stephen Eyears, has left the organisation, coinciding with a change to its…
I was getting into the elevator today, running back and forth between managing a long-term vendor project and keeping things…
After the Anthem mega-breach, questions abound about possible abuses of medical data. Here is a breakdown that offers some context….
Packed with real-world scenarios, hands-on techniques, and insights into widely used tools, the third edition of the bestselling Ultimate Kali…
This is for the people who believe in God, and believe in the power of prayer. The next time you…