A Facebook hack that allowed attackers to remotely delete any photo they wanted to from the social network has been…
Sunshine Coast Council is tapping into an AI-enabled kiosk to handle in-person queries at its municipal centre via an Azure…
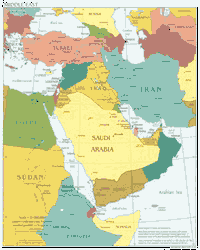
Most people–especially in the West–know very little about the Middle East and the people that live there. This lack of…
Jamie Oliver’s website was affected by a malware issue, a spokesperson for the British celebrity chef has told the BBC….
Semperis has published the results of a new study looking at cyberattacks against water and electricity operators across the U.S….
I made a prediction a couple months before the original iPhone came out that features would not be the deciding…
Lenovo’s installation of a security-breaking app called Superfish on some computers has customers justifiably angry, but some folks are now…
With support from the UK Cyber League, the advisory was jointly produced by the National Cyber Security Centre (NCSC UK) and…
Google has unveiled Firebase Studio, a groundbreaking cloud-based platform designed to streamline the creation of full-stack AI applications. This innovative…
The Baader-Meinhof pheonomenon is kind of like Deja Vu in the sense that it’s something weird that many people have…
A report by HP has found that 44 percent of all of the breaches in 2014 were caused by known…
Hackers intercepted and monitored the emails of over 103 bank regulators at the Office of the Comptroller of the Currency…