Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Major media outlets globally reported Feb. 21, 2025 that a $1.5 billion (USD) hack of Bybit was a record-setting cyberattack. The…
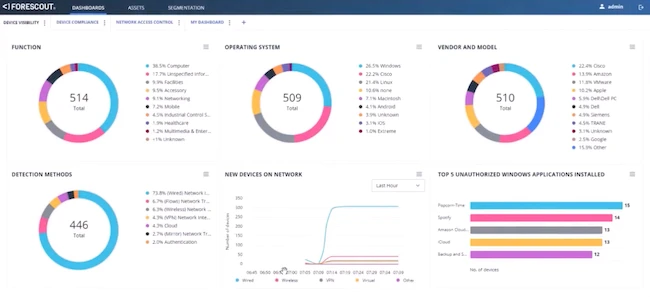
Forescout announced new Forescout eyeScope cloud visibility and monitoring solution, expanding the Forescout 4D Platform to the cloud. Forescout also…
When you next type something sensitive on your computer keyboard, be sure that no-one else is watching. A recent case…
The US Treasury’s OCC disclosed an undetected major email breach for over a year Pierluigi Paganini April 09, 2025 The…
So, speaking from a general perception standpoint, Indians are considered Asians because they’re on the Asian sub-continent. Well, at least…
It’s that time of year again! Here at Detectify, we’re excited to celebrate the talent and dedication of our Crowdsource…
Gcore, the global edge AI, cloud, network, and security solutions provider, has launched Super Transit, a cutting-edge DDoS protection and…
Enzoic for AD Lite Password Auditor is an innovative tool designed to integrate with an organization’s Active Directory environment seamlessly….
U.S. CISA adds Gladinet CentreStack and ZTA Microsoft Windows Common Log File System (CLFS) Driver flaws to its Known Exploited…
The goal of socialism should be to iterate itself out of existence. Its purpose is to keep negative aspects of…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…