The religious love to claim Einstein as their own. They do so because the misinterpret his remarks referring to nature…
Microsoft has uncovered a sophisticated ransomware campaign exploiting a zero-day vulnerability in the Windows Common Log File System (CLFS), tracked…
Apr 09, 2025Ravie LakshmananApplication Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical…
At RSA this year I caught a talk by a Google executive that discussed what makes Google’s Information Security team…
GCHQ’s National Cyber Security Centre (NCSC), in collaboration with international and industry partners, has issued a global alert regarding two…
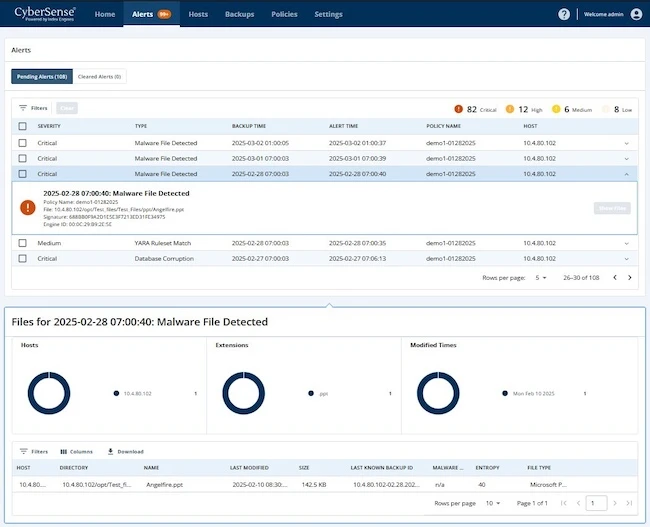
Index Engines announced CyberSense 8.10, fully integrated with Dell PowerProtect Cyber Recovery, which provides new capabilities to enhance cyber resilience…
Apr 09, 2025Ravie LakshmananVulnerability / Ransomware Microsoft has revealed that a now-patched security flaw impacting the Windows Common Log File…
The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Exploited Vulnerabilities (KEV) Catalog, adding two new vulnerabilities…
I enjoy doing a little trick whenever I can with strangers. Whenever the opportunity arises, I like to ask complete…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding active exploitation of a critical vulnerability in…
The OpenSSL Project has released version 3.5.0 of its widely used open-source cryptographic library, introducing new features and notable changes…
The government has handed the Post Office £136m more in taxpayer’s money towards its core technology transformation project. This is…