The recent cyberattack attributed to the “Holy League Coalition” hacking group has raised significant concerns about cybersecurity, as key British…
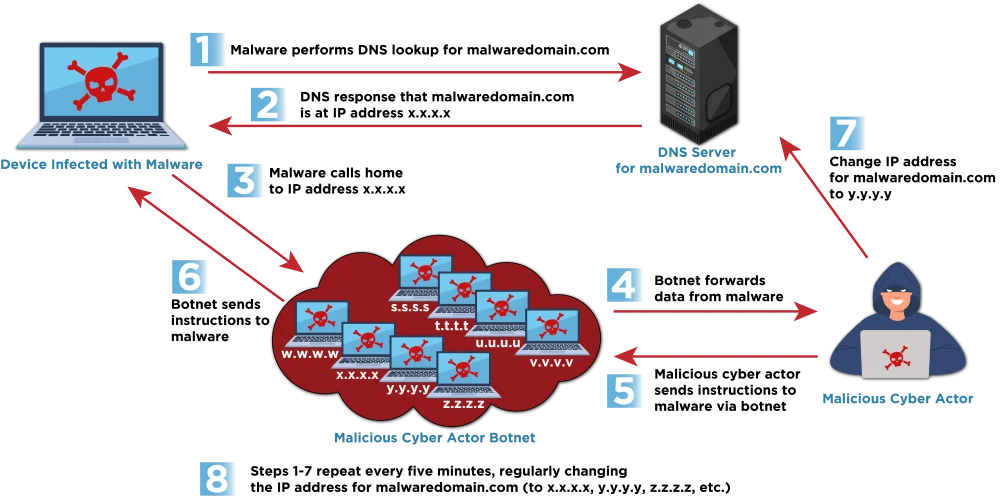
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), alongside the National Security Agency (NSA), the Federal Bureau of Investigation (FBI),…
First off, let me just say that I am a serious Ron Paul supporter. I’ve blogged about him, spammed promoted…
A Chinese official has been arrested after succumbing to a “honey trap” overseas and supplying classified information to a foreign…
Apr 07, 2025Ravie LakshmananCloud Security / Cryptocurrency A malicious campaign dubbed PoisonSeed is leveraging compromised credentials associated with customer relationship…
Scott Adams has posted another highly inflammatory post — this time claiming that popular evidence for evolution is bullshit. I’m…
In a world where wars are no longer fought on battlefields alone, the Philippines is confronting an invisible but no…
The US Cybersecurity and Infrastructure Security Agency (CISA) has officially released Version 2.0.0 of the NICE Workforce Framework for Cybersecurity,…
On April 3, 2025, Ivanti disclosed an unauthenticated buffer overflow vulnerability tracked as CVE-2025-22457, affecting multiple Ivanti products. Australian organizations…
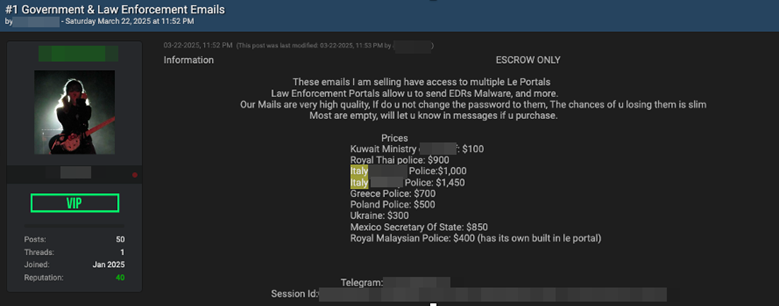
EDR-as-a-Service makes the headlines in the cybercrime landscape Pierluigi Paganini April 07, 2025 Cybercriminals exploit compromised accounts for EDR-as-a-Service (Emergency…
I need some help here. I have a friend with whom I’m debating evolution. He is a fundamentalist Christian (wait…
Hong Kong police have smashed a fraud syndicate and arrested six suspects who allegedly cheated at least 12 victims out…