IT company Pure Storage has appointed Altay Ayyuce as area vice president of Australia and New Zealand. He replaces Amy…
Alinta Energy has gradually replaced most of the Azure-based services that once powered its data architecture with Databricks, an effort…
I wrote recently about learning to differentiate between blogspam and self-submitted content on meritocracy-based sites like Digg and Reddit. My…
Hong Kong Commissioner of Police Raymond Siu Chak-yee has said he expects the city’s law and order to continue to…
In today’s security world, there are numerous security solutions that can limit access to company data and IT resources and…
Thousands of people swooned in a dark conference hall that felt more like a rock concert when a Microsoft product…
Everyone loves Google. They want to be everything to everyone, and they’re getting pretty damn good at it. Once you…
Scams can happen in the blink of an eye as cybercriminals race to move stolen money before victims, banks and…
The Australian Cyber Security Centre is advising users of certain Next.js versions to upgrade to the latest version after the…
Meta Platforms released the latest version of its large language model (LLM) Llama, called the Llama 4 Scout and Llama…
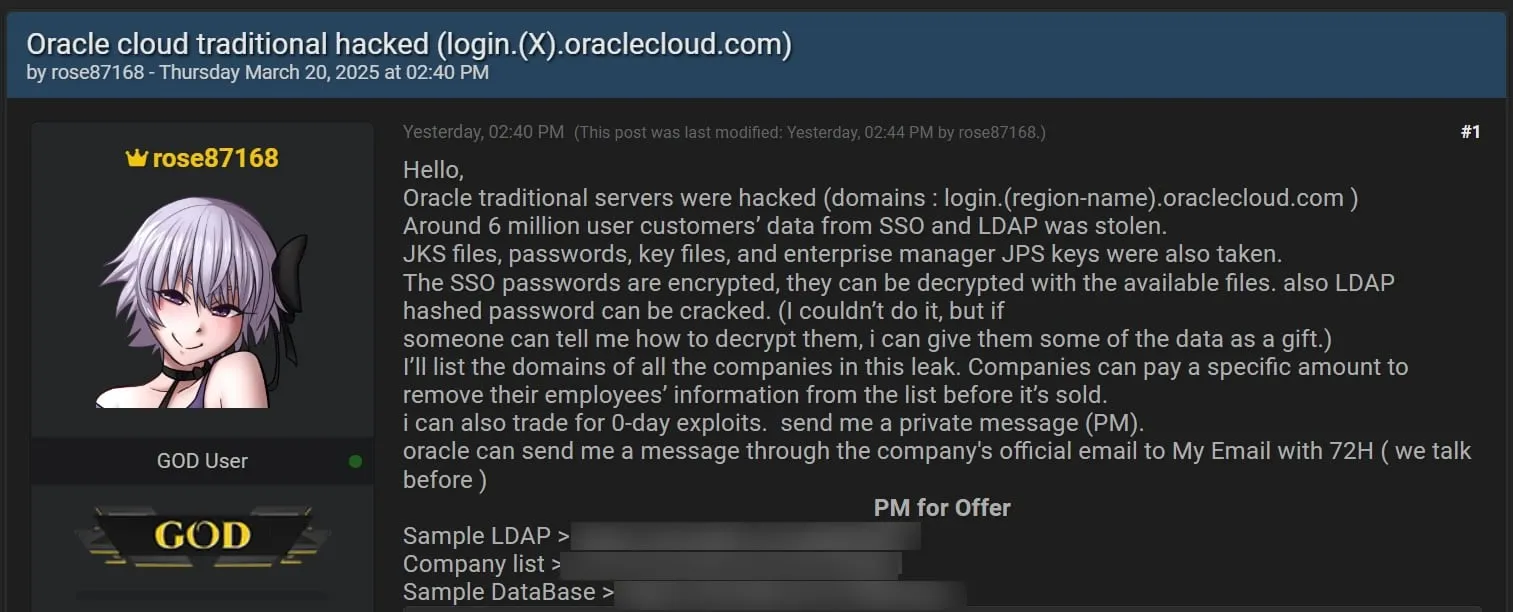
Oracle privately notifies Cloud data breach to customers Pierluigi Paganini April 06, 2025 Oracle confirms a cloud data breach, quietly…
DEFCON is a Social Networking EventDEFCON makes all of the audio and video content available (for a price) afterwards, meaning…





![Why You Should Encrypt ALL of Your Google Activities [POC] Why You Should Encrypt ALL of Your Google Activities [POC]](https://image.cybernoz.com/wp-content/uploads/2025/04/Why-You-Should-Encrypt-ALL-of-Your-Google-Activities-POC.png)