By now we’re all quite familiar with the Bush administration’s stance on security. It essentially boils down to the best…
We’re all familiar with the occasional maulings that take place during language translation, and most of them are harmless enough…
[ PUBLISHED: Jun 1, 2007 ] Those of us who use RSS tend to struggle constantly with two impulses: 1)…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Attackers are probing Palo Alto…
Expert used ChatGPT-4o to create a replica of his passport in just 5 minutes bypassing KYC Pierluigi Paganini April 06,…
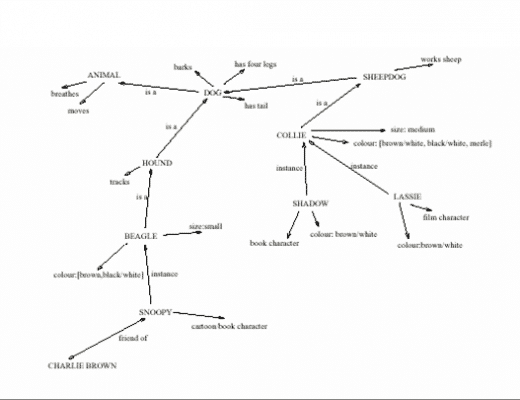
No technology interests me more than the semantic web. I have no doubt that I will spend many years working…
Most guys know about the nice guy paradox. It’s where they’ve been told since they were young — both by…
The United States has successfully extradited two Kosovo nationals, Ardit Kutleshi, 26, and Jetmir Kutleshi, 28, from Kosovo to face…
I was just taking a shower and had a frightening idea. With all this talk of the National ID program,…
Ransomware file decryptor tools are essential for recovering data encrypted by malicious software without paying ransoms. These tools help victims…
Those of you who read this site know that I’ve been heavily promoting Ron Paul as a candidate for President…
Microsoft Outlook will enforce stricter authentication requirements for high-volume senders, impacting domains that send over 5,000 emails daily. These changes,…

![Did Jesus Teach Racism? [Matthew 15:23] Did Jesus Teach Racism? [Matthew 15:23]](https://image.cybernoz.com/wp-content/uploads/2025/04/Did-Jesus-Teach-Racism-Matthew-1523.jpg)
![How To Effectively Manage and Process Your RSS Feeds [GTD] How To Effectively Manage and Process Your RSS Feeds [GTD]](https://image.cybernoz.com/wp-content/uploads/2025/04/How-To-Effectively-Manage-and-Process-Your-RSS-Feeds-GTD.png)