Many who are new to networking and security wonder what it means to have “ports” open on your computer. Some…
Google has made a big move to fight cyber threats by announcing Sec-Gemini v1, an experimental AI model designed to…
Kubernetes has become the backbone of modern cloud native applications, and as adoption grows, organizations increasingly seek to consolidate workloads…
Being an information security consultant I am often asked how to balance the need for online passwords that are both…
A recently discovered set of vulnerabilities, dubbed “IngressNightmare,” found in Ingress NGINX Controller, exposing clusters to unauthenticated remote code execution…
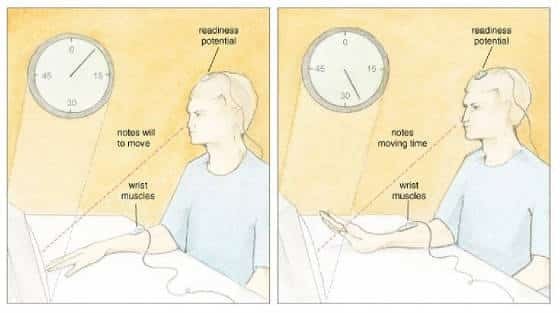
One of the more interesting sub-debates associated with Atheism vs. Religion is that of free will. Quite simply, many Atheists…
Yesterday I wrote about Joanna Rutkowska’s work that highlighted a serious security flaw in Windows Vista. Her finding was that…
Too Many Organizations Look to Scheduled Audits to Dictate Patching Efforts Though it may seem obvious that patches to critical…
Since getting my watch I’ve received some pretty interesting reactions from people. The biggest misconception people seem to have about…
I’ve recently started searching my site using Google rather than using the built-in WordPress search. That’s nothing new — pretty…
I know you don’t believe me, as we’ve had this conversation before. But there will come a time in your…
President Bush isn’t the hateful warmonger people make him out to be. I agree that he’s hurting the United States…