I’ve recently been toiling with the issue of listing credentials in my email signature. Since I’ve had anything to put…
A privilege escalation vulnerability in Google Cloud Platform (GCP), dubbed “ImageRunner,” was recently discovered and fixed. The flaw, which Tenable…
Utimaco launched Quantum Protect, the Post Quantum Cryptography application package for its u.trust General Purpose HSM (Hardware Security Modules) Se-Series….
Apr 02, 2025Ravie LakshmananCryptojacking / Malware Cybersecurity researchers have shed light on an “auto-propagating” cryptocurrency mining botnet called Outlaw (aka…
The past year has been crucial for Ukrainian-British tech cooperation. As one of the leading IT service exporters, Ukraine’s presence…
I’ve been experiencing growing frustration with social/political issues lately, and each time I get to thinking about various problems that…
A critical security alert has been issued to WordPress site administrators following the discovery of two high-severity vulnerabilities in the…
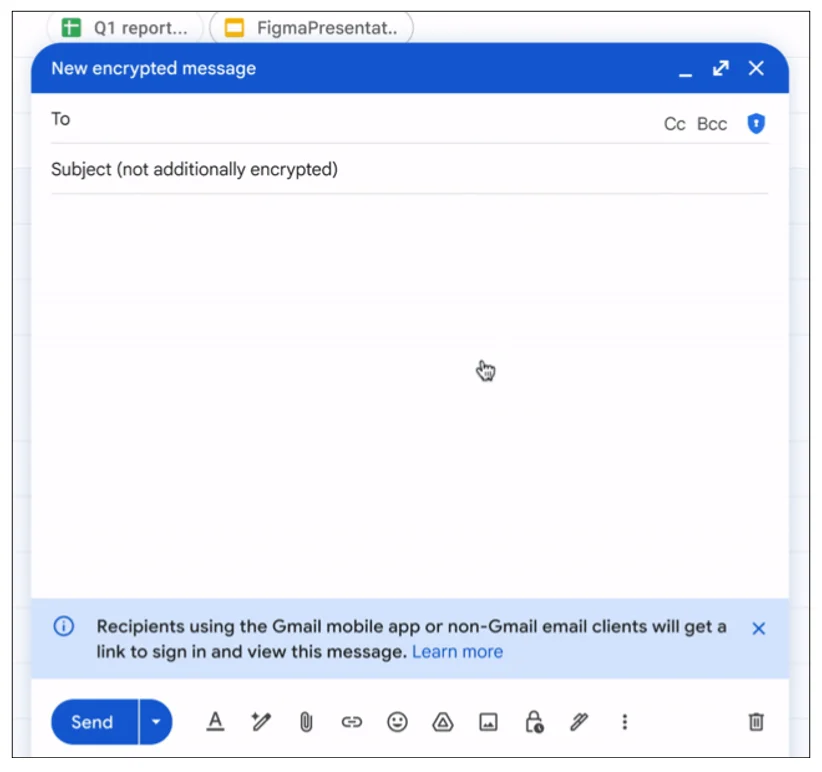
Sending end-to-end encrypted (E2EE) emails from Gmail enterprise accounts is about to become much easier than it is now, Google…
Apr 02, 2025The Hacker NewsCompliance / Data Protection Introduction As the cybersecurity landscape evolves, service providers play an increasingly vital…
Dozens of technology firms are continuing to put the lives and livelihoods of supply chain workers at risk by failing…
Of course, nearly everyone is familiar with one main concept — the well-worn and widely known view that Windows file…
As LinkedIn’s chief product officer (CPO), Tomer Cohen oversees the teams responsible for product management, user experience and design, and…