More and more I’ve run into a particular dilemma in life, and I think it’s worth exploring a bit. As…
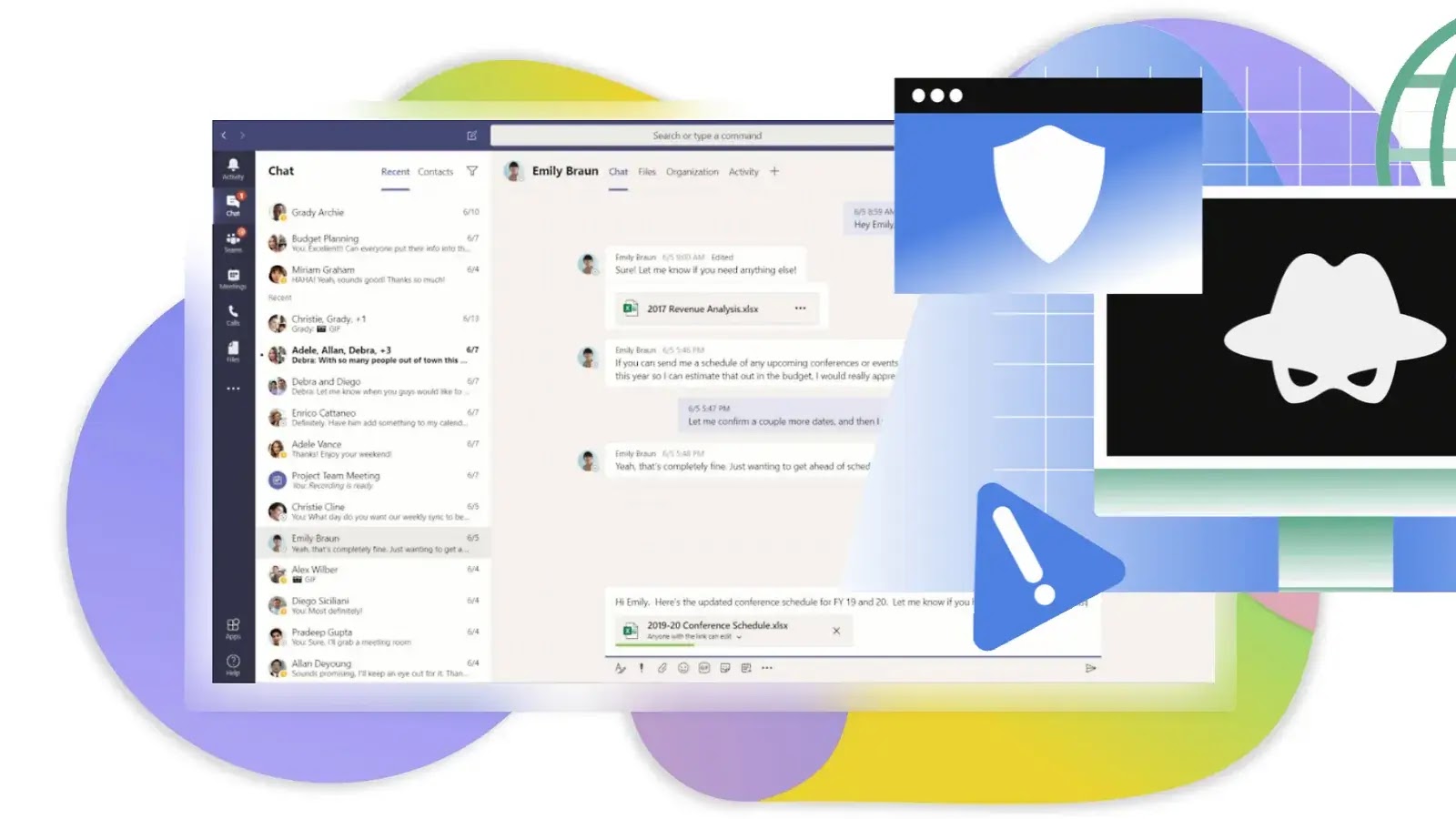
Cybersecurity experts have uncovered a new malware campaign targeting Microsoft Teams users to infiltrate corporate systems. By exploiting the platform’s…
The platform where people forget their passwords the most is YouTube, leading with the highest number of password-related searches. Video…
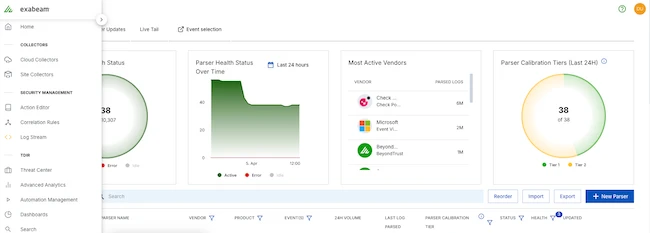
Exabeam unveiled Exabeam Nova, an autonomous AI agent delivering actionable intelligence that enables security teams to respond faster to incidents,…
Apr 02, 2025Ravie LakshmananRansomware / Email Security The financially motivated threat actor known as FIN7 has been linked to a…
In an effort to enhance Thailand’s cybersecurity infrastructure, the National Cyber Security Agency (NCSA) and Google Cloud have announced a…
One of the comments “How To Fix The Internet” article that’s circulating is the notion of a central organization (like…
The Python Software Foundation (PSF) has officially announced the adoption of a new standardized lock file format, outlined in PEP 751….
Royal Mail Data Breach: 144GB of Sensitive Information Now Available for Sale Royal Mail has recently made headlines after falling…
Wikiphilian. MedicalA mental illness characterized by the irrational conviction that any problem faced by a group can be rendered solvable…
A surge in cyber activity targeting critical edge technologies and management tools, including SonicWall, Zoho, F5, Ivanti, and other systems,…
With the rapid advancement of artificial intelligence (AI), deepfake technology has emerged as a significant cybersecurity threat. Deepfakes, which use…