Mar 12, 2019 — Nothing has helped me more in life than this system. I use it to this day….
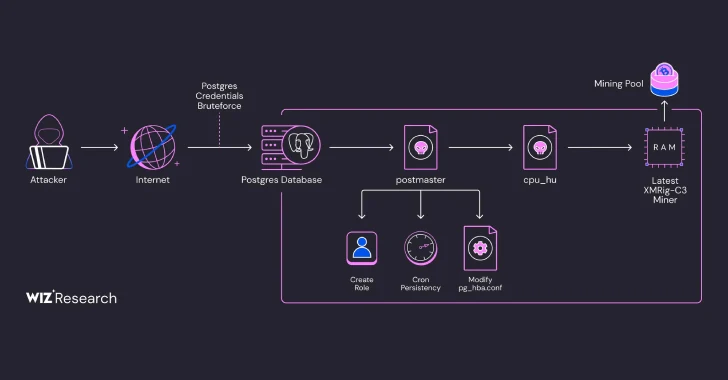
Apr 01, 2025Ravie LakshmananCryptojacking / Cloud Security Exposed PostgreSQL instances are the target of an ongoing campaign designed to gain…
This blog post points out some very interesting philisophical issues with Pixar’s new movie “The Incredibles”. I noticed the two…
The Democratic Party has filed a lawsuit against the Trump administration over its elections executive order, arguing the president lacks…
The Acronis Threat Research Unit (TRU) was presented with an interesting threat chain and malware sample for analysis that involved…
Below is a list of three articles/stories that every single geek absolutely must be aware of and be willing to…
Sam’s Club confirmed it is investigating a possible cyberattack after the retailer was referenced on a leak site by the…
Autorité de la concurrence, France’s antitrust watchdog, has fined Apple €150 million ($162 million) for using the App Tracking Transparency…
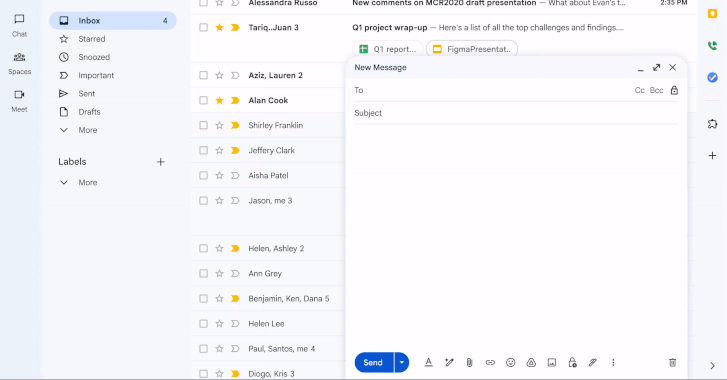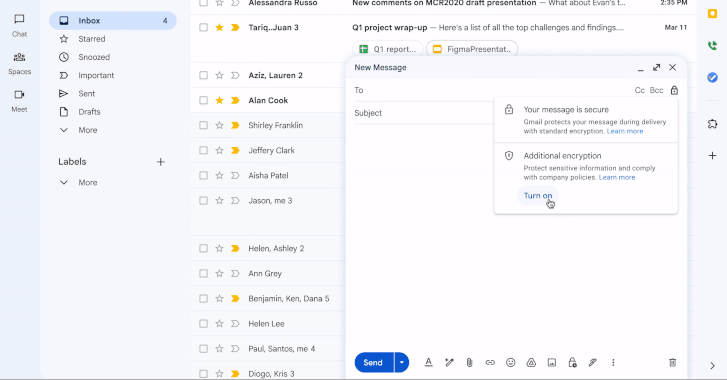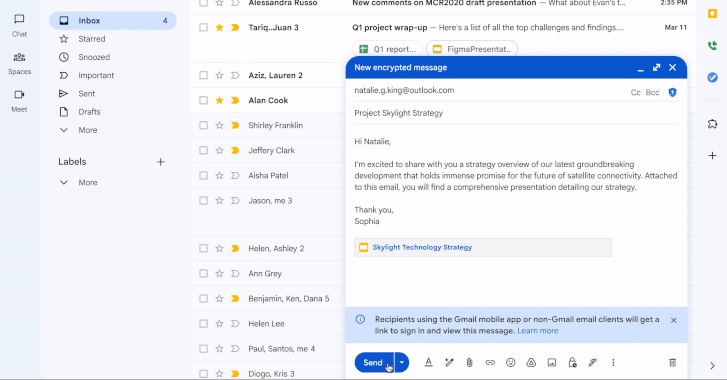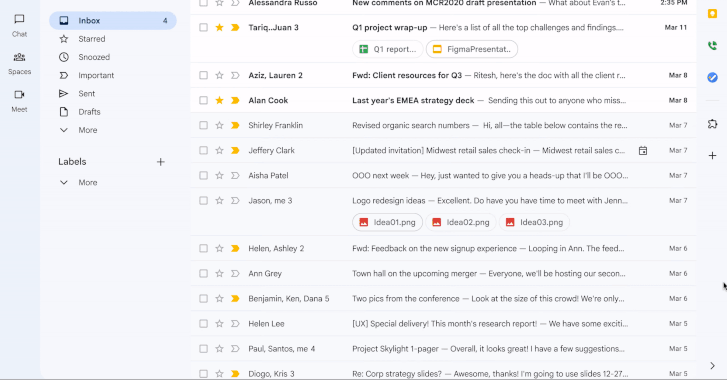
Apr 01, 2025Ravie LakshmananEncryption / Email Security On the 21st birthday of Gmail, Google has announced a major update that…
Well, after reading Linux’s comments on interpreted languages and discussing the matter with Ken some, I have come to the…
A critical vulnerability in CrushFTP’s file transfer server software has come under attack less than a week after the flaw…
Microsoft has disclosed the discovery of multiple critical vulnerabilities within the GRUB2, U-Boot, and Barebox bootloaders, leveraging its AI-driven Security…