The cryptocurrency world feels like a wild ride full of risks, twists, and big dreams of building wealth. In its…
The Microsoft Fabric Community Conference, currently underway from March 31 to April 2, 2025, in Las Vegas, has already become…
It seems my writing has gone from something of an experiment/curiosity to something different. I am not sure what that…
Check Point Software Technologies has confirmed a data breach following claims by threat actor CoreInjection on March 30th, 2025, but…
Users of Apple devices in the UK are “at the most risk in the world” of being hacked, following a…
Xiaofeng Wang, a well-respected computer scientist and professor at Indiana University, has suddenly vanished along with his wife, Nianli Ma….
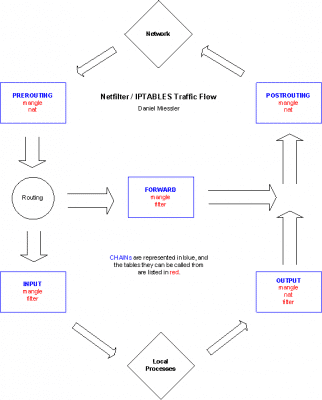
iptables is the packet filtering technology that’s built into the 2.4 Linux kernel. It’s what allows one to do firewalling,…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical Cisco vulnerability to its Known Exploited Vulnerabilities (KEV) catalog…
In what can be described as a significant security breach, over 1.5 million personal photographs have been exposed and are…
Tax season is in full force, and with the filing deadline fast approaching on April 15, scammers are happy to…
Well, I have published another article after over a year without doing so, and this time it has met with…
Microsoft has discovered multiple critical vulnerabilities affecting widely used bootloaders including GRUB2, U-Boot, and Barebox. These security flaws potentially expose…