Rockwell Automation has identified a critical flaw in its Verve Asset Manager software, exposing industrial systems to potential exploitation. The vulnerability, tracked…
New Jersey passed a new cybersecurity regulation in January 2025. This makes the state the latest to implement strong rules…
Canon Marketing Japan Inc. and Canon Inc. have issued an important security update regarding a vulnerability in certain printer drivers….
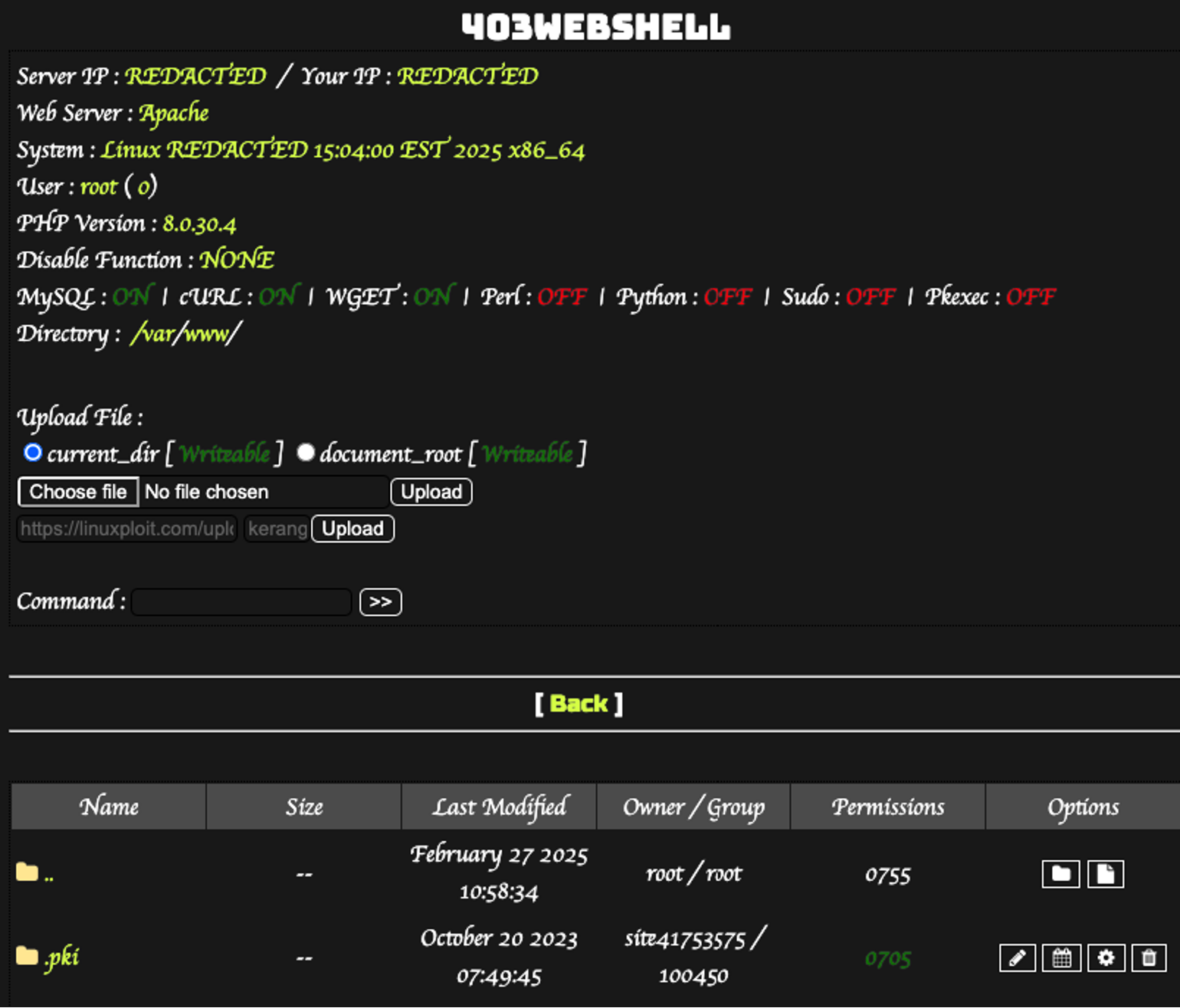
Hiding WordPress malware in the mu-plugins directory to avoid detection Pierluigi Paganini April 01, 2025 Sucuri researchers spotted threat actors…
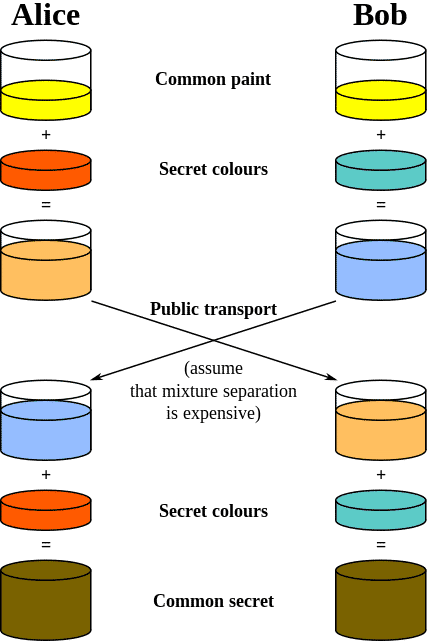
Diffie-Hellman is a key exchange protocol developed by Diffie and Hellman (imagine that) in 1976. The purpose of Diffie-Hellman is…
Apple has issued an urgent security advisory concerning three critical zero-day vulnerabilities CVE-2025-24200, CVE-2025-24201, and CVE-2025-24085 that have been actively…
Introduction The rise of Agentic AI has become one of the most talked about trends in the AI world. The…
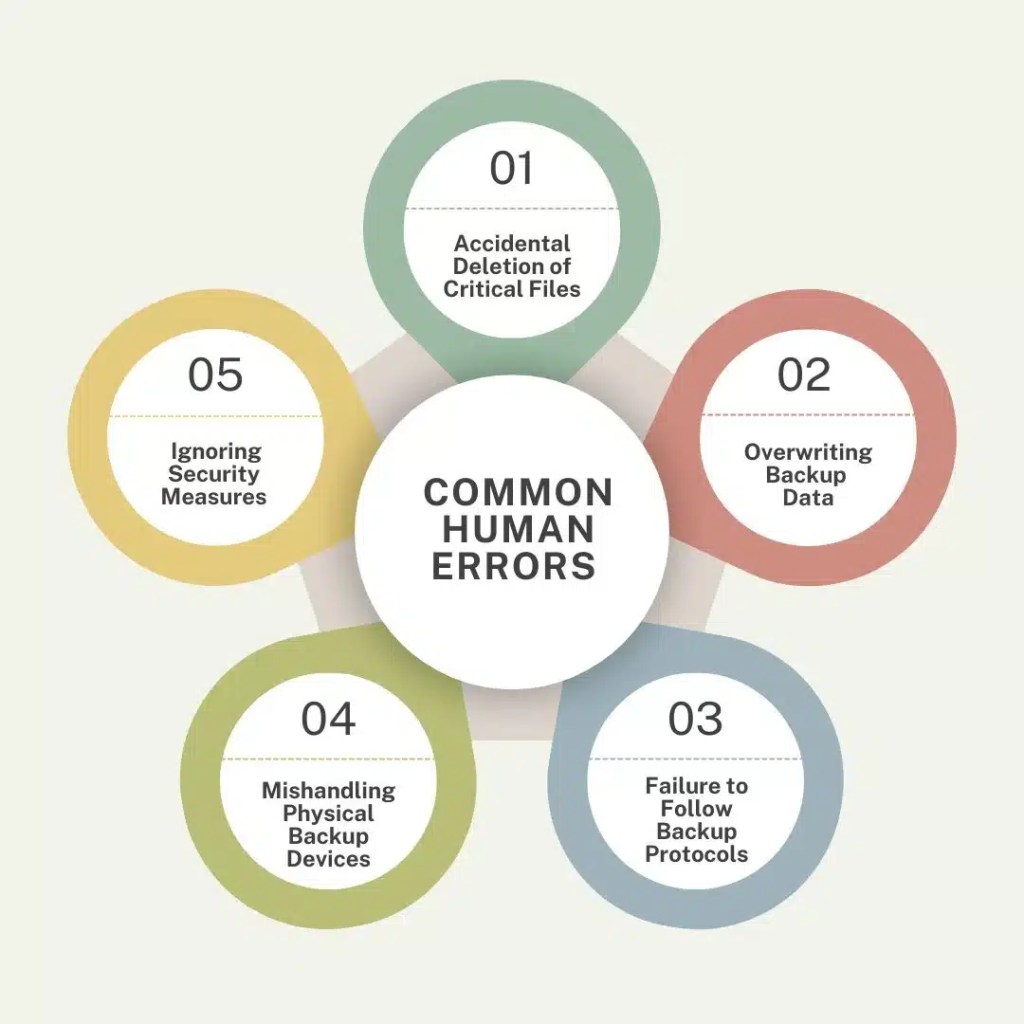
World Backup Day, observed annually on March 31, serves as a reminder of the importance of protecting data against cyber…
The time has come to dump Internet Explorer. I know, I know — you may have heard the same thing…
Security researchers have confirmed active exploitation attempts targeting the critical authentication bypass vulnerability in CrushFTP (CVE-2025-2825) following the public release…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a security advisory warning organizations about a critical vulnerability in Cisco’s…
We live in a time where technology is changing fast, and artificial intelligence is becoming part of everything we do….