I think Trump’s conviction might be the American Left’s version of Brexit. Let me explain. First off, I think Trump…
In the digital graveyard, a new threat stirs: Out-of-support devices becoming thralls of malicious actors 27 Aug 2024 • ,…
The Cybersecurity Maturity Model Certification (CMMC) is a cybersecurity framework designed to protect Federal Contract Information (FCI) and Controlled Unclassified…
Forescout Vedere Labs has uncovered 46 new vulnerabilities in solar power systems, primarily affecting inverters from three leading manufacturers Sungrow,…
Mar 28, 2025Ravie LakshmananEndpoint Security / Threat Intelligence Cybersecurity researchers are calling attention to a new sophisticated malware called CoffeeLoader…
I think I’ve finally figured out what’s up with podcast audio. At least in terms of: So what I’m going…
Many cyber experts are panning a new Trump administration executive order that would shift more responsibilities for responding to cyberattacks…
The discovery of the NGate malware by ESET Research is another example of how sophisticated Android threats have become 28…
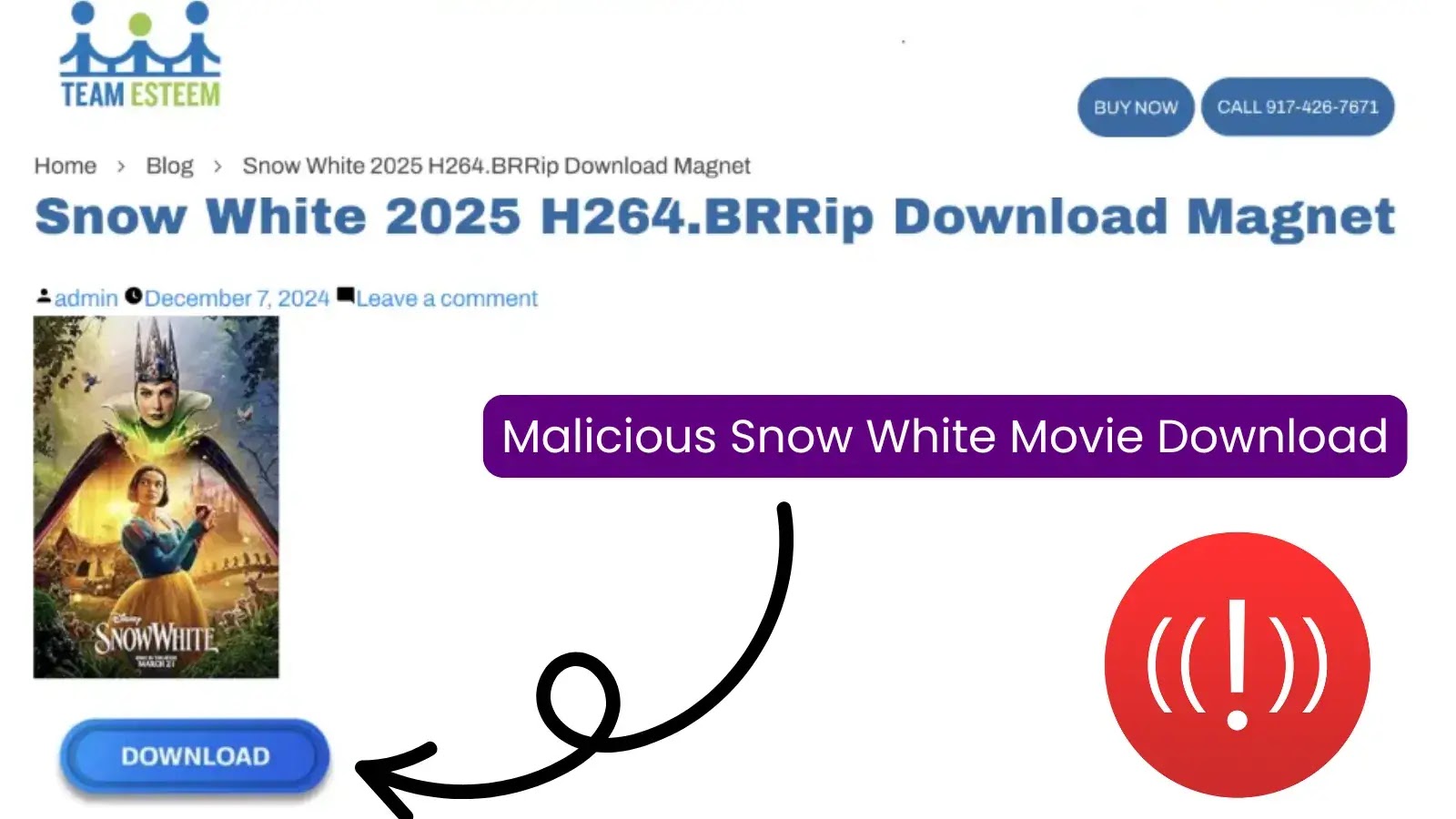
As the latest adaptation of Snow White hits theaters with lukewarm reception, the absence of streaming options on platforms like…
Cloud adoption is here to stay, and as its use continues to accelerate across enterprises, so does the need for…
Continue reading online to avoid the email cutoff issue SECURITY | AI | MEANING :: Unsupervised Learning is my continuous…
Sometimes there’s more than just an enticing product offer hiding behind an ad 03 Sep 2024 • , 3 min….