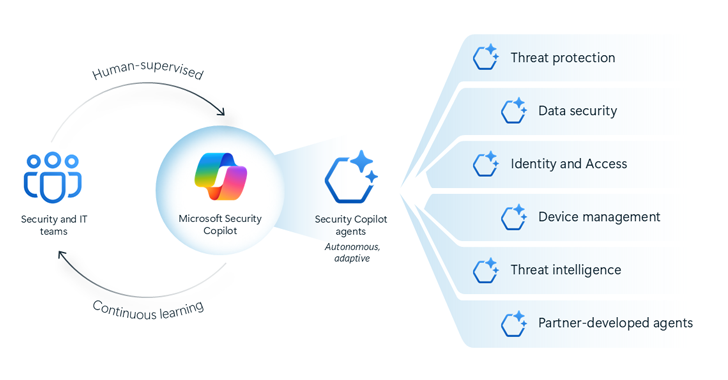
Mar 24, 2025Ravie LakshmananEnterprise Security / Browser Security Microsoft on Monday announced a new feature called inline data protection for…
SECURITY | AI | MEANING :: Unsupervised Learning is my continuous stream of original ideas, story analysis, tooling, and mental…
Keep your cool, arm yourself with the right knowledge, and other tips for staying unshaken by fraudsters’ scare tactics 25…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory regarding a critical zero-day vulnerability in Google Chrome…
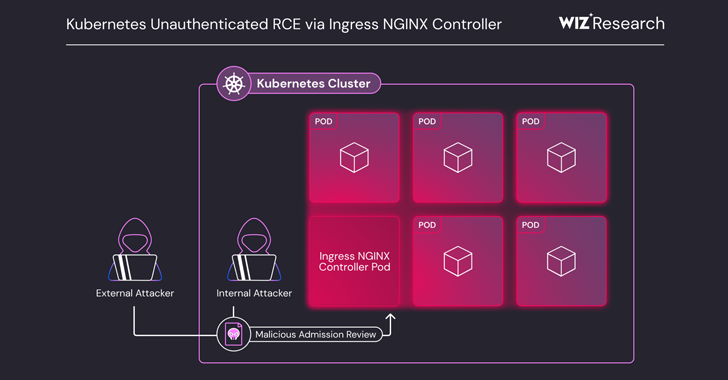
Mar 24, 2025Ravie LakshmananVulnerability / Cloud Security A set of five critical security shortcomings have been disclosed in the Ingress…
I think a hidden tendency towards a belief in Libertarian free will is at the root of people’s opinion that…
ESET Research has conducted a comprehensive technical analysis of Gamaredon’s toolset used to conduct its cyberespionage activities focused in Ukraine…
Law enforcement authorities in seven African countries have arrested 306 suspects and confiscated 1,842 devices as part of an international…
SECURITY | AI | MEANING :: Unsupervised Learning is a stream of original ideas, story analysis, tooling, and mental models…
ESET research examines the group’s malicious wares as used to spy on targets in Ukraine in the past two years…
Mar 25, 2025Ravie LakshmananMobile Security / Data Theft Cybersecurity researchers are calling attention to an Android malware campaign that leverages…
Table of Contents I have been thinking a lot about the competition between OpenAI, Anthropic, Meta, and Google for who…