The European Telecommunications Standards Institute (ETSI) has this week debuted its first post-quantum cyber security standard, designed to guarantee the…
CORS vulnerabilities discovered in Go implementations. AI meeting assistant launch, web hacking activity guide. Successful SEO frameworks shared for AI…
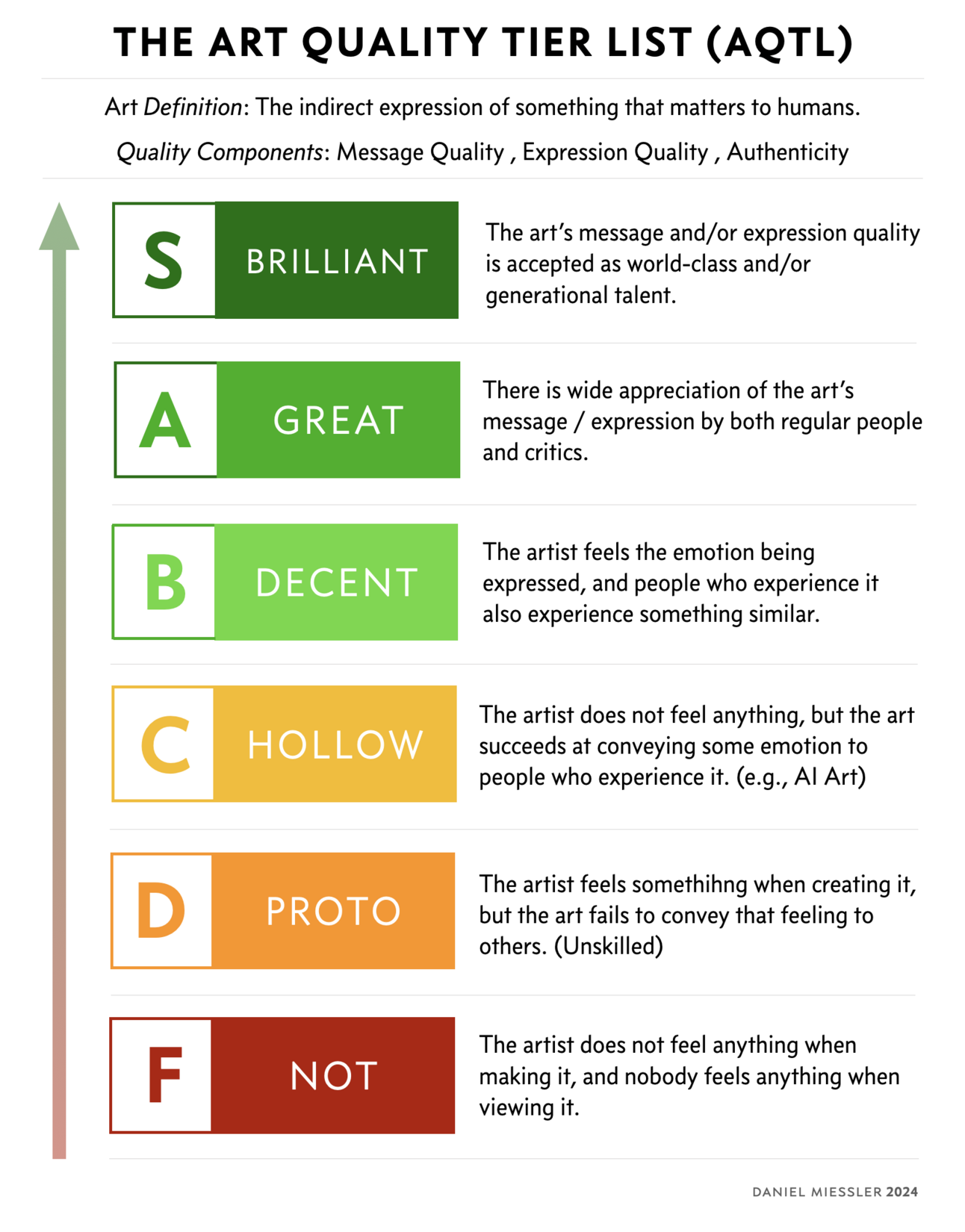
I think I finally figured out what art is. Took me decades. Here’s my definition, which has two primary components:…
Ever alert to fresh money-making opportunities, fraudsters are blending physical and digital threats to steal drivers’ payment details 15 Oct…
When people think of cybersecurity threats, they often picture external hackers breaking into networks. However, some of the most damaging…
The Science, Innovation and Technology Committee has questioned tech experts on the government’s plans for the digital centre of government…
Security vulnerabilities exposed in multiple platforms, New AI tools reshape meeting notes and voice processing, Developer workflow optimized through terminal…
I think InfoSec—and in fact business management in general—is evolving into the combination of four things: Policy (entity identity/goals) State…
Google Project Zero’s LLM-powered variant analysis, deobfuscating IAM polices and a real-time SCP error monitor, using LLMs to create secure…
“Hey, wanna chat?” This innocent phrase can take on a sinister meaning when it comes from an adult to a…
Ten npm packages were suddenly updated with malicious code yesterday to steal environment variables and other sensitive data from developers’…
Mar 26, 2025Ravie LakshmananBrowser Security / Vulnerability Google has released out-of-band fixes to address a high-severity security flaw in its…





![[tl;dr sec] #255 – AI finds 0day in SQLite, Cloud Security Tools, Auto-generate Terraform Secure Guardrails [tl;dr sec] #255 - AI finds 0day in SQLite, Cloud Security Tools, Auto-generate Terraform Secure Guardrails](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-255-AI-finds-0day-in-SQLite-Cloud.png)

