Biometric data refers to unique physical or behavioral characteristics that are used to verify a person’s identity. Revoking or changing…
This is a sad story that illustrates how losing your ID can effectively ruin your life and reputation. 19-year-old dual…
Mar 26, 2025Ravie LakshmananMalware / Vulnerability The Chinese threat actor known as FamousSparrow has been linked to a cyber attack…
The Spring Budget is expected to play a pivotal role in advancing the UK’s AI ambitions. If the government gets…
A network of companies operated by a secretive Chinese tech firm has been trying to recruit recently laid-off US government…
In partnership with The internet is wild right now. Yesterday’s meme coin is today’s fortune. Social media musical chairs. Here’s…
Android malware campaigns use .NET MAUI to evade detection Pierluigi Paganini March 25, 2025 Researchers warn of a new Android…
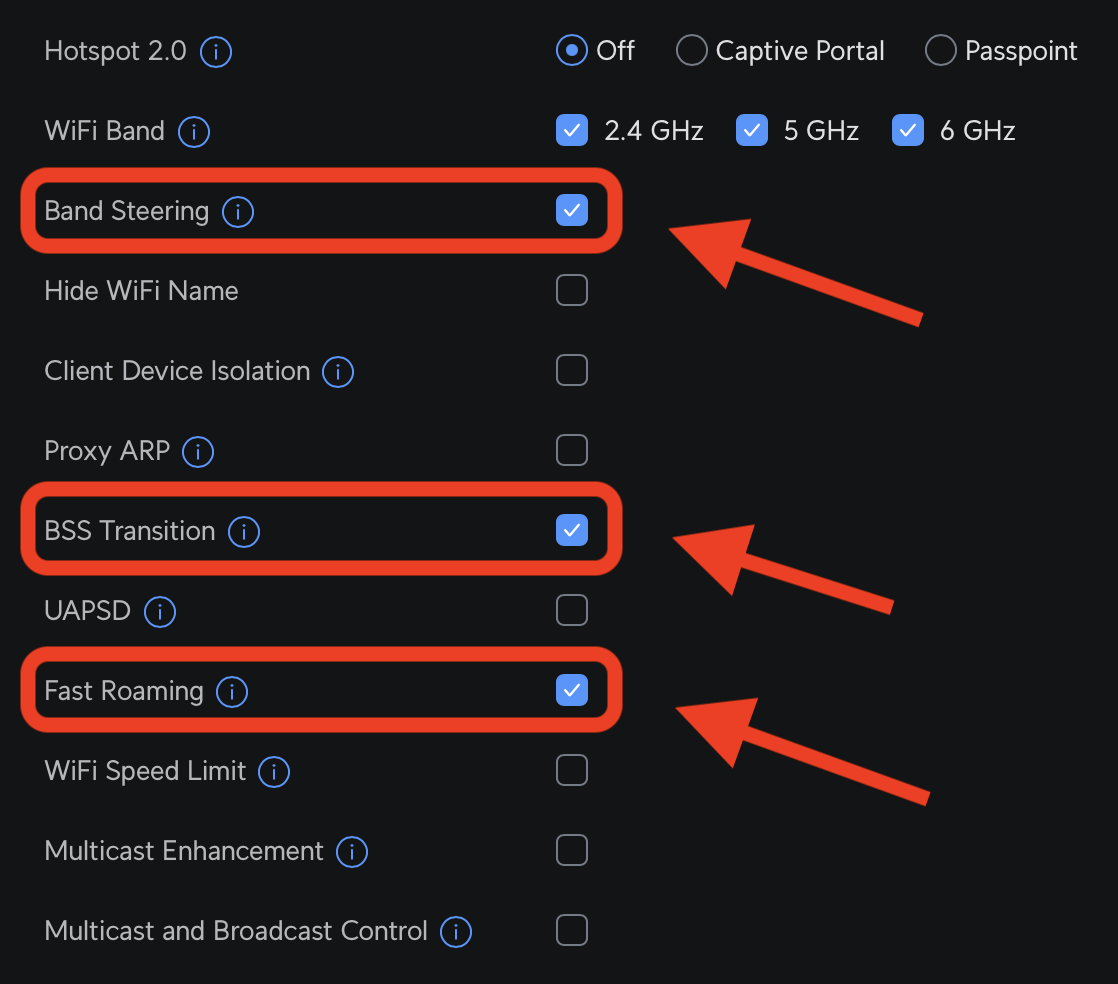
The three settings I had to enable to get proper WiFi roaming The problem I’m a massive fan of Ubiquiti…
How Google eliminates vuln classes, human expert-level AI spear phishing, how Palantir hardens their code writing process I hope you’ve…
A Canadian citizen is one step closer to standing trial in the United States for his alleged involvement in a…
The trailblazing scientist shares her reasons for hope in the fight against climate change and how we can tackle seemingly…
You can’t escape AI in WhatsApp even if you are based in one of the 41 European countries. Today, more…






![[tl;dr sec] #265 – Google’s Secure-by-Design Web Framework, AI-powered Phishing, How Palantir Secures Source Control [tl;dr sec] #265 - Google's Secure-by-Design Web Framework, AI-powered Phishing, How Palantir Secures Source Control](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-265-Googles-Secure-by-Design-Web-Framework-AI-powered-Phishing.png)


