SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
Jun 13, 2024 Resolving ZAP 2.15 Crashes on macOS with Java Version Issues Recently, I encountered persistent crashes while running…
I hope you’ve been doing well! Recently Overheard It’s late so you must forgive me for the brief intro. Some…
Researchers warn that attackers could exploit a recently discovered critical vulnerability in the open-source JavaScript framework Next.js to bypass authorization…
What is the most common pain point facing businesses these days? Is it supply chain fragility? Fierce competition? Tight cashflows?…
Microsoft says a known issue is causing Remote Desktop freezes on Windows Server 2025 systems after installing security updates released since…
A sophisticated macOS malware loader platform known as “ReaderUpdate” has significantly evolved its capabilities, with researchers identifying new variants written…
As cyber threats continue to surge, businesses face growing pressure to fortify their defences and ensure operational continuity. Regulatory frameworks…
As the Trump administration’s Department of Government Efficiency (DOGE) continues to rampage through the United States federal government, essentially guided…
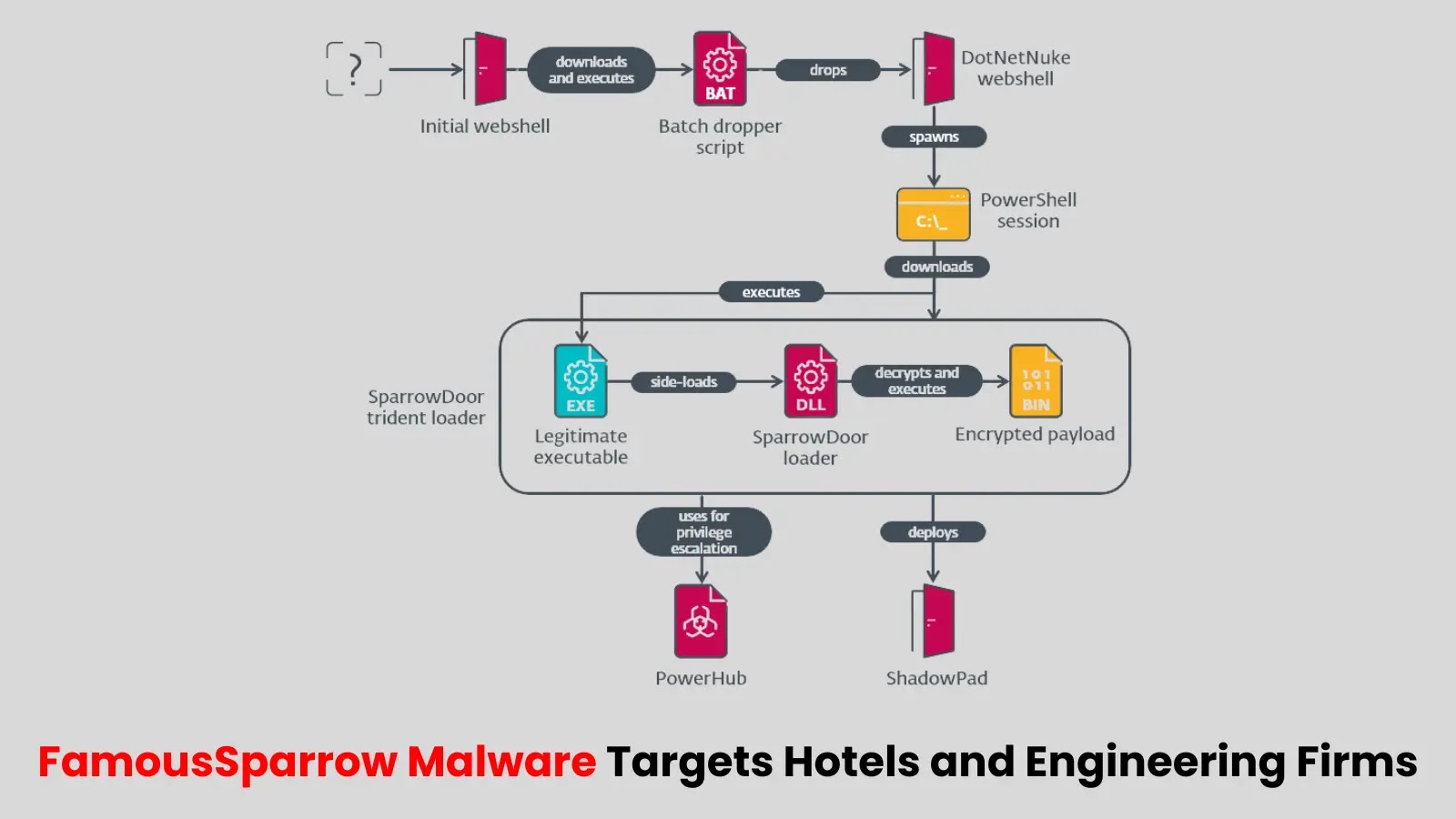
ESET researchers have uncovered new activity from the China-aligned APT group FamousSparrow, revealing two previously undocumented versions of their custom…
Security researchers at ReversingLabs have discovered a new malware campaign on the npm package repository, revealing a new approach to…
Too much of a good thing is always problematic, and cybersecurity tools are no exception. Corporate teams juggle a surplus…


![[tl;dr sec] #266 – AI CVE Analysis, Hijacking Abandoned S3 Buckets, Doing Less in AppSec [tl;dr sec] #266 - AI CVE Analysis, Hijacking Abandoned S3 Buckets, Doing Less in AppSec](https://image.cybernoz.com/wp-content/uploads/2025/03/tldr-sec-266-AI-CVE-Analysis-Hijacking-Abandoned-S3.png)