The backdoor can execute commands and lets attackers download additional modules onto the victim’s machine, ESET research finds 26 Nov…
INTERPOL led a multi-national law enforcement operation dubbed “Operation Red Card,” which has resulted in the arrest of over 300…
How aware are you that your personal information could be bought and sold without your consent—and that there are companies…
Security is hard. It’s even harder now that, apparently, the UK Government has secretly ordered Apple to reduce the security…
Dive Brief: Researchers from GreyNoise on Thursday reported active exploitation of CVE-2025-24813, a critical remote code execution vulnerability in Apache Tomcat…
ESET researchers make a discovery that signals a shift on the UEFI threat landscape and underscores the need for vigilance…
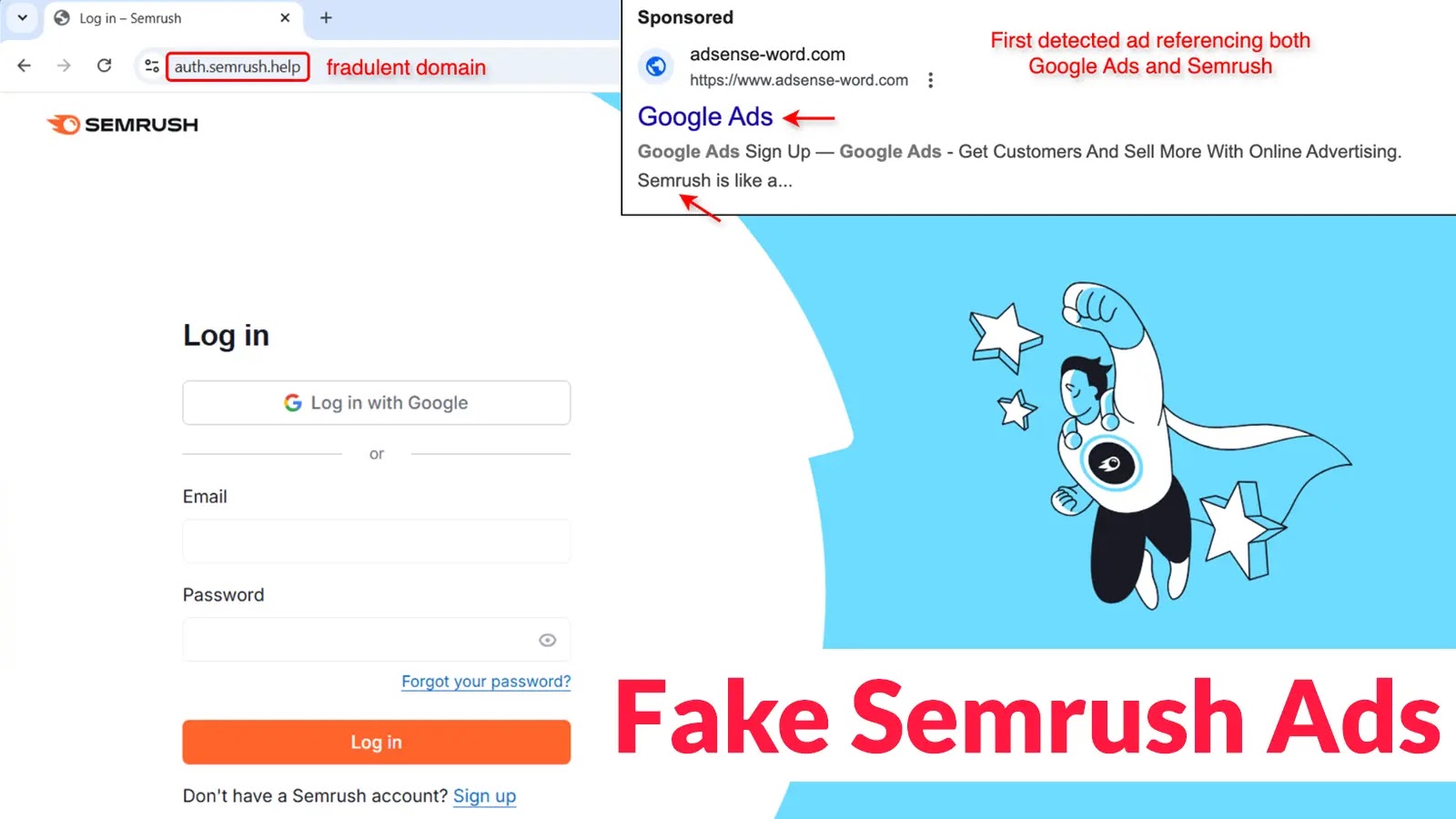
A sophisticated phishing campaign targeting Google account credentials through fake Semrush advertisements has emerged, posing a significant threat to digital…
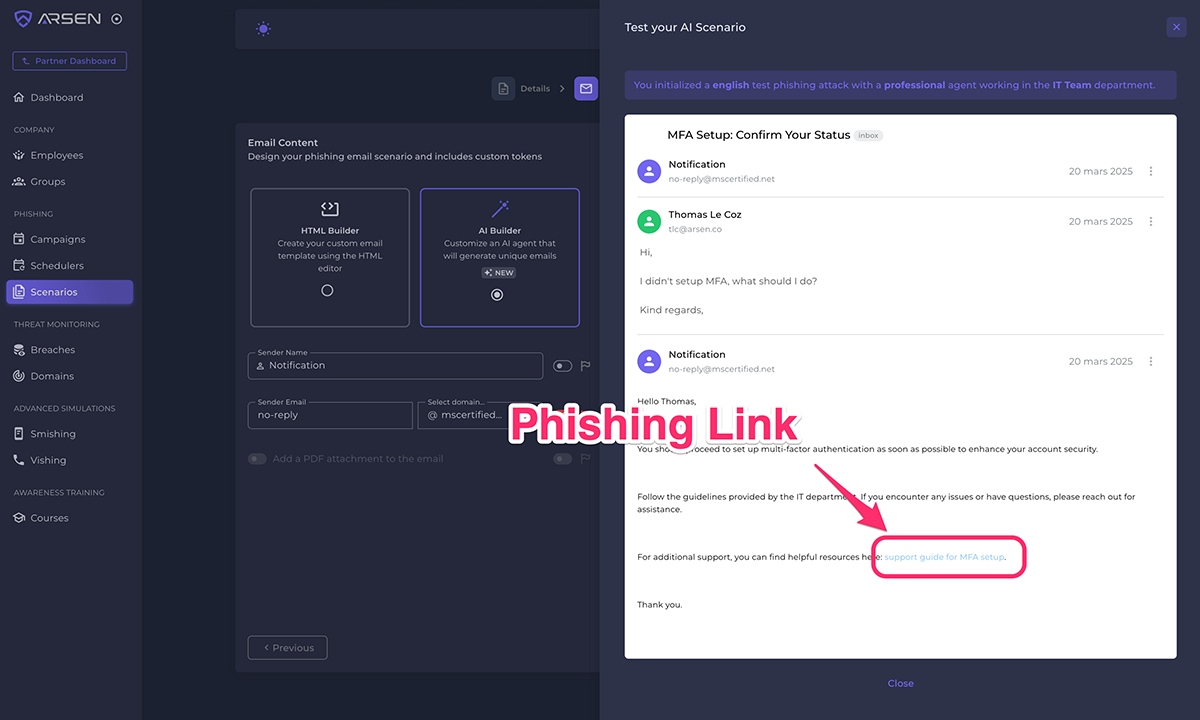
Paris, France, March 24th, 2025, CyberNewsWire Arsen, a leading cybersecurity company specializing in social engineering defense, today announced the full…
In recent years, intelligence agencies in Western countries have reached a troubling conclusion: North Korea, led by Kim Jong Un,…
Mar 24, 2025Ravie LakshmananMalware / Ransomware A ransomware-as-a-service (RaaS) operation called VanHelsing has already claimed three victims since it launched…
Sean Green, interim CIO at Birkbeck, University of London, tells Computer Weekly that the promise of the university of the…
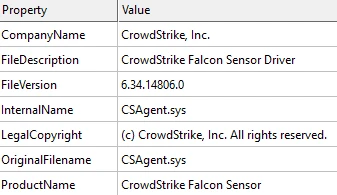
Medusa ransomware uses malicious Windows driver ABYSSWORKER to disable security tools Pierluigi Paganini March 24, 2025 Medusa ransomware uses a…