A cybercriminal collective, known as Cloak, has confirmed its involvement in an attack targeting the Virginia attorney general’s office in…
As cybersecurity is a make-or-break proposition for businesses of all sizes, can your organization’s security strategy keep pace with today’s…
Google has recently rolled out a critical security update for its Chrome browser, addressing vulnerabilities that could potentially allow attackers…
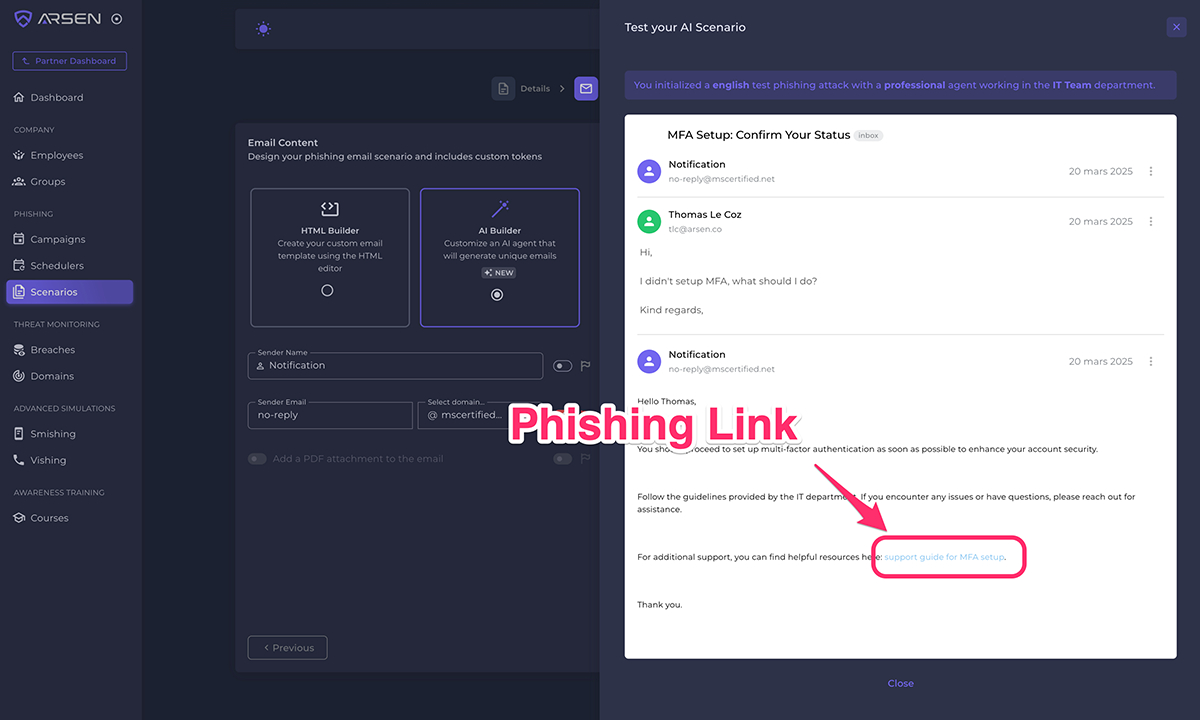
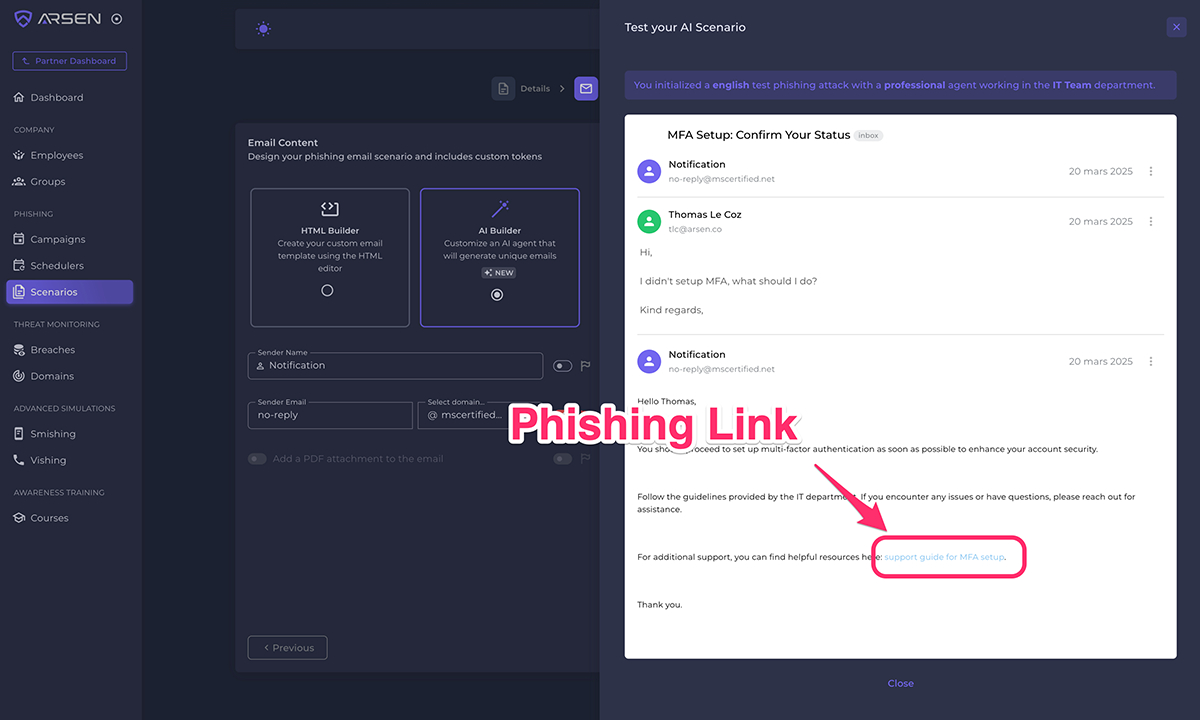
Paris, France, March 24th, 2025, CyberNewsWire Arsen, a leading cybersecurity company specializing in social engineering defense, today announced the full…
Paris, France, March 24th, 2025, CyberNewsWire Arsen, a leading cybersecurity company specializing in social engineering defense, today announced the full…
Mar 24, 2025Ravie LakshmananVulnerability / Web Security A critical security flaw has been disclosed in the Next.js React framework that…
South Africa-listed poultry producer Astral Foods (ARLJ.J) has reported a cybersecurity incident that disrupted its operations and is expected to…
Could attackers use seemingly innocuous prompts to manipulate an AI system and even make it their unwitting ally? 12 Dec…
A new strain of malware, known as SvcStealer, has emerged as a significant threat in the cybersecurity landscape. This malware…
iProov launched iProov Workforce MFA. This device-independent, FIDO Alliance-certified, biometric authentication solution helps organizations mitigate the risk of one of…
Oracle has put forward its AI Agent Studio for Fusion Applications as a platform for orchestrating artificial intelligence (AI) agents…
Aggregate vulnerability scores don’t tell the whole story – the relationship between a flaw’s public severity rating and the specific…