Cybercriminals are skilled at using public information to their advantage. Knowing how they gather this data can help you protect…
U.S. Treasury removed sanctions against the crypto mixer service Tornado Cash Pierluigi Paganini March 22, 2025 The U.S. Treasury is…
Cybercriminals are abusing Microsoft’s Trusted Signing platform to code-sign malware executables with short-lived three-day certificates. Threat actors have long sought after…
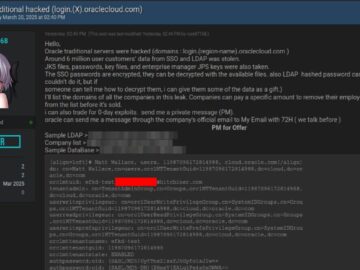
A recent investigation by CloudSEK’s XVigil platform has uncovered a cyberattack targeting Oracle Cloud, resulting in the exfiltration of six…
Recent advances in generative artificial intelligence (AI) are making it increasingly difficult to know the difference between what is real…
There are various circumstances in which a given person might conceivably seek to convert horsepower (hp) to kilowatts (kW). They…
Mar 22, 2025Ravie LakshmananFinancial Security / Cryptocurrency The U.S. Treasury Department has announced that it’s removing sanctions against Tornado Cash,…
The 2025 NVIDIA GPU Technology Conference (GTC) showcased groundbreaking advancements and innovations in the field of AI and quantum computing….
Zero-day broker Operation Zero offers up to $4 million for Telegram exploits Pierluigi Paganini March 22, 2025 Russian zero-day broker…
The UK’s National Cyber Security Centre (NCSC), working alongside the Department for Science, Innovation and Technology (DSIT), has enlisted the…
Researchers have determined that Coinbase was the primary target in a recent GitHub Actions cascading supply chain attack that compromised…
A new phishing campaign has been tricking users into giving out access to their Meta Business accounts especially Instagram. The…