A new malware campaign has been uncovered, involving a sophisticated stealer known as Arcane, which is distributed through YouTube videos…
This blog post was co-authored with Elie Berreby, Senior SEO Strategist Criminals are highly interested in online marketing and advertising…
If your organization is like many, annual penetration testing may be a regular part of your security protocols. After completing…
A sophisticated network of suspected North Korean IT workers has been discovered leveraging GitHub to create false identities and secure…
Symantec’s Threat Hunter team has identified a sophisticated custom backdoor named “Betruger” linked to a RansomHub affiliate. This newly discovered…
Cybersecurity researchers at the Citizen Lab at the University of Toronto have exposed the use of sophisticated spyware named Graphite,…
The UK’s National Cyber Security Centre (NCSC) has published specific timelines on migrating to post-quantum cryptography (PQC), dictating that critical…
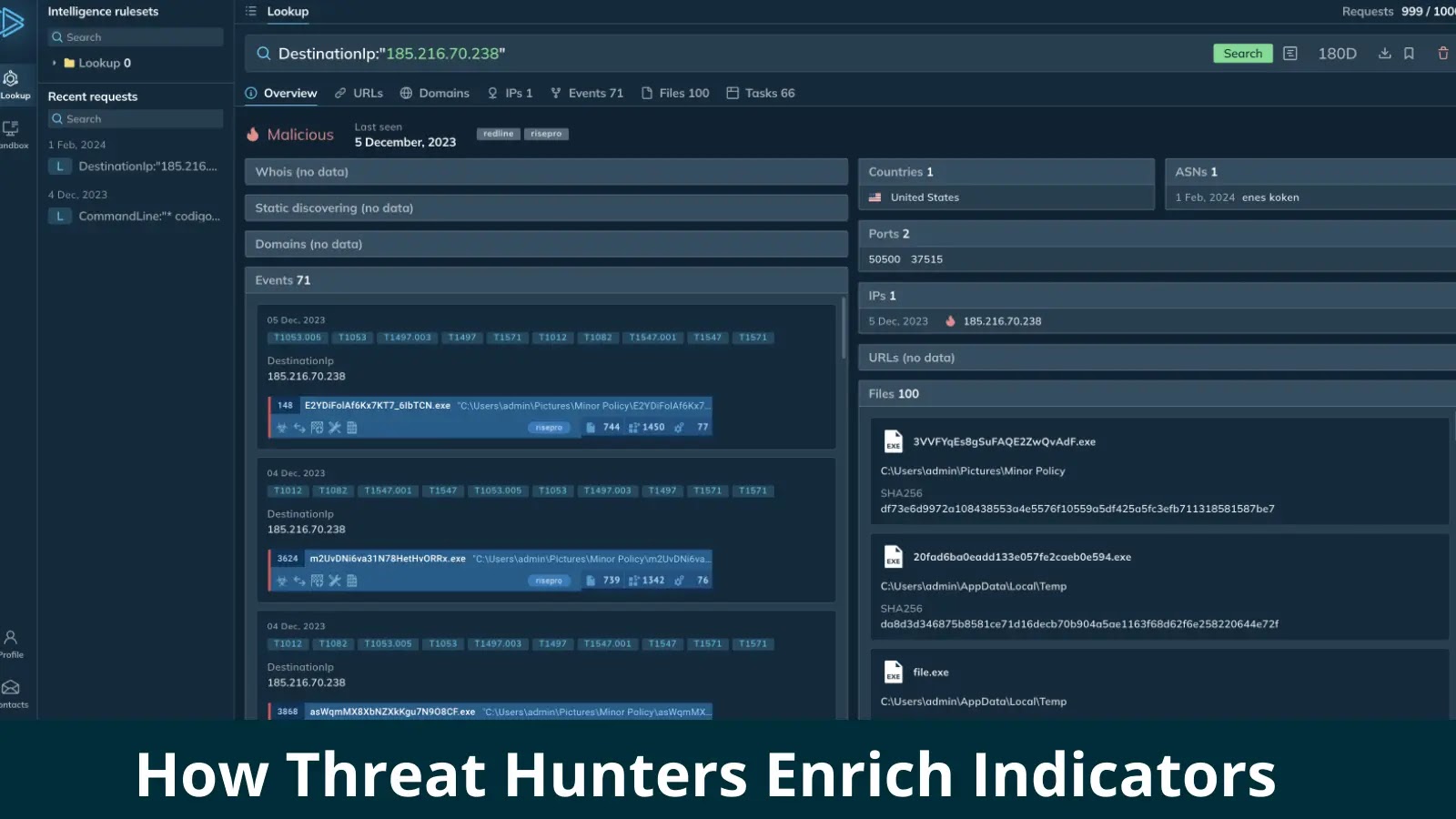
While data is king, context is his queen — together, they reign over domains that thrive on research, analysis, discovery,…
A recent cybersecurity threat has been identified, where steganographic malware is being distributed through seemingly innocuous JPEG image files. This…
Dive Brief: Johannes Ullrich of the SANS Internet Storm Center reported exploitation attempts this week against two critical Cisco vulnerabilities…
A newly identified custom backdoor deployed in several recent ransomware attacks has been linked to at least one RansomHub ransomware-as-a-service…
Microsoft experienced a widespread outage on March 19, 2025, affecting Outlook on the web services. The tech giant has attributed…