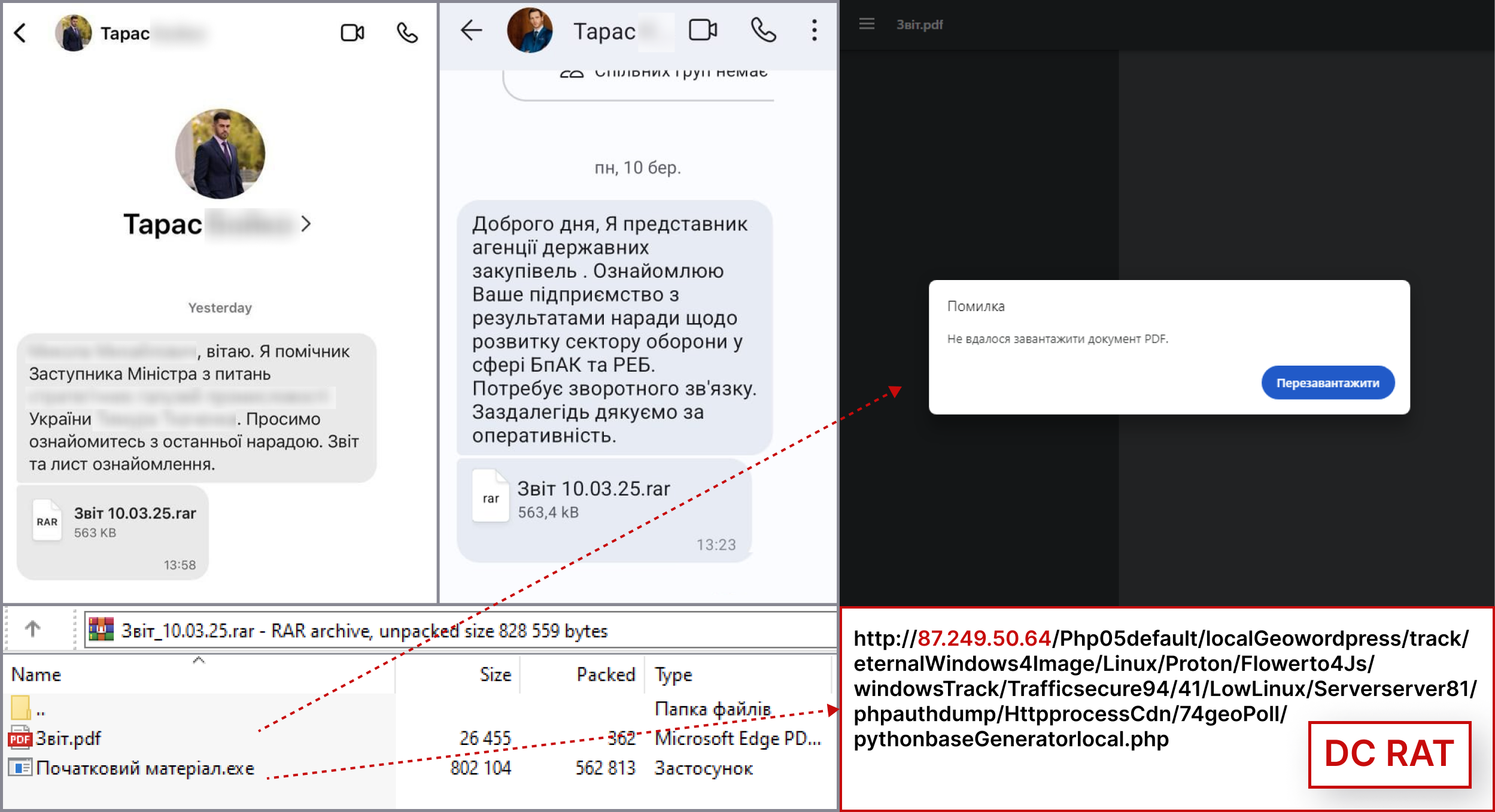
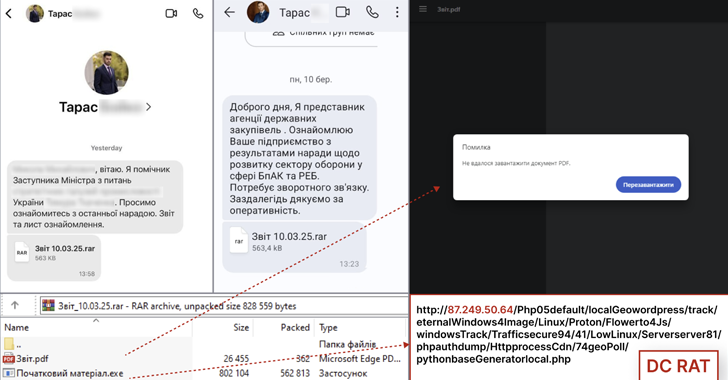
CERT-UA warns of cyber espionage against the Ukrainian defense industry using Dark Crystal RAT Pierluigi Paganini March 20, 2025 CERT-UA…
The Chinese Advanced Persistent Threat (APT) group known as Salt Typhoon, also referred to as FamousSparrow, GhostEmperor, Earth Estries, and…
In December the Kyiv Post reported of the Ukrainian military’s own long-range, tethered drones, that, “currently about 40 percent of…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding a critical vulnerability found in Edimax IC-7100…
The Babuk ransomware group has recently claimed responsibility for a sophisticated cyberattack on Orange, a leading global telecommunications company. According…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about a serious vulnerability in the NAKIVO Backup…
A severe vulnerability in the Linux kernel has remained undetected for nearly two decades, allowing local users to gain root…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about a serious vulnerability in the NAKIVO Backup…
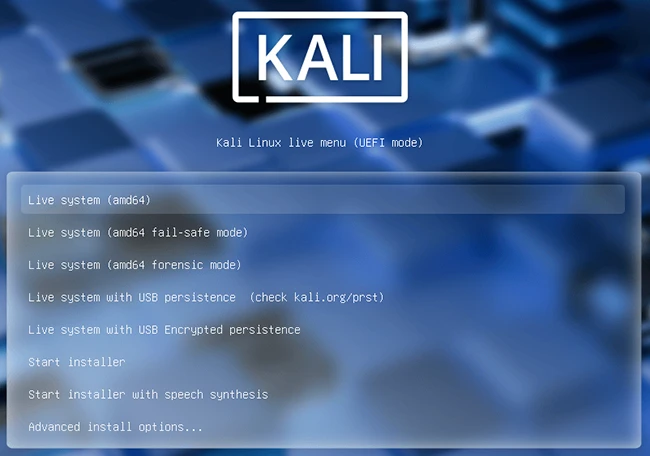
Kali Linux 2025.1a is now available. This release enhances existing features with improvements designed to streamline your experience. 2025 theme…
Mar 20, 2025Ravie LakshmananCybercrime / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign…
A sophisticated attack vector dubbed “MalDoc in PDF” allows threat actors to bypass traditional security scanning by embedding malicious Word…
SpyX, a company known for developing spyware, has experienced a data breach that compromised the personal information of nearly 2…