In this Help Net Security interview, Sunil Seshadri, EVP and CSO at HealthEquity, talks about the growing risks to healthcare…
California Cryobank LLC, one of America’s largest sperm donor repositories, has confirmed a significant data breach that exposed sensitive customer…
Despite growing national security concerns and government restrictions, Chinese military-linked companies remain deeply embedded in the US digital supply chain,…
A sophisticated attack employing Legacy Driver Exploitation technique has emerged as a significant cybersecurity threat, according to a recent security…
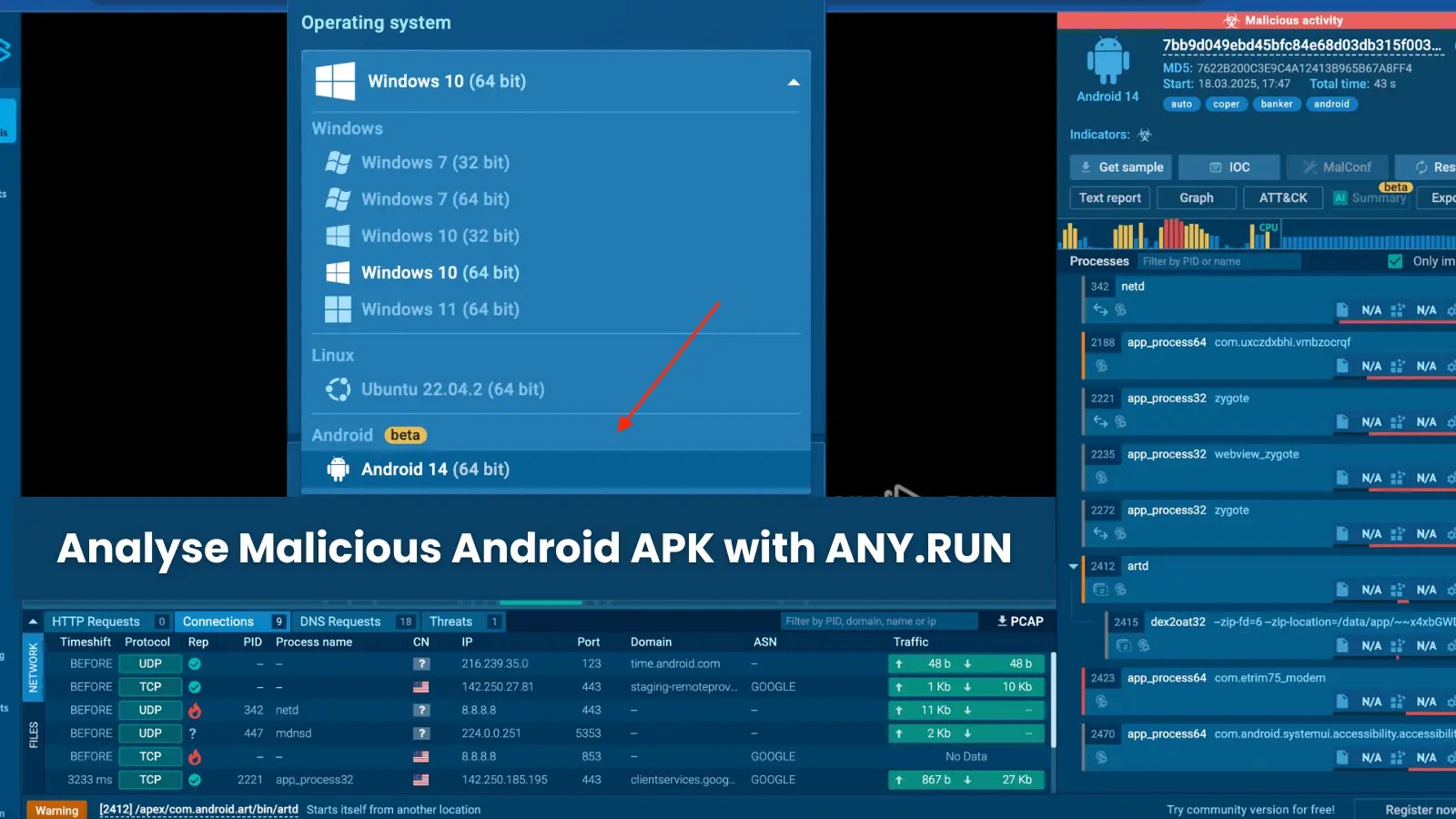
ANY.RUN, the interactive malware analysis platform has announced full support for Android OS in its cloud-based sandbox environment, enabling security…
Cybersecurity experts have identified a persistent trend of threat actors exploiting legitimate remote monitoring and management (RMM) software to infiltrate…
Moving Beyond Detection to Real-Time, Automated Security Across Workloads, Cloud, and Infrastructure SecPod, a global cybersecurity provider, has announced the…
Organised crime gangs are turning to AI-powered scams and payment systems to target victims, allowing them to rapidly and more…
Kali Linux, the widely acclaimed cybersecurity-focused distribution, has officially unveiled its latest release, Kali Linux 2025.1a. This update not only significantly enhances desktop environments but also…
The Australian Epilepsy Project (AEP) aims to build a dataset on epilepsy and tap AI and cloud to help industry…
ASX-listed engineering firm Worley is using Dell and Nvidia technology to underpin its development of generative AI applications. The firm…
Ukraine’s Computer Emergency Response Team (CERT-UA) is warning about highly targeted attacks employing compromised Signal accounts to send malware to…