Google was hit with two charges of breaching landmark EU rules on Wednesday, while Apple was ordered to help rivals…
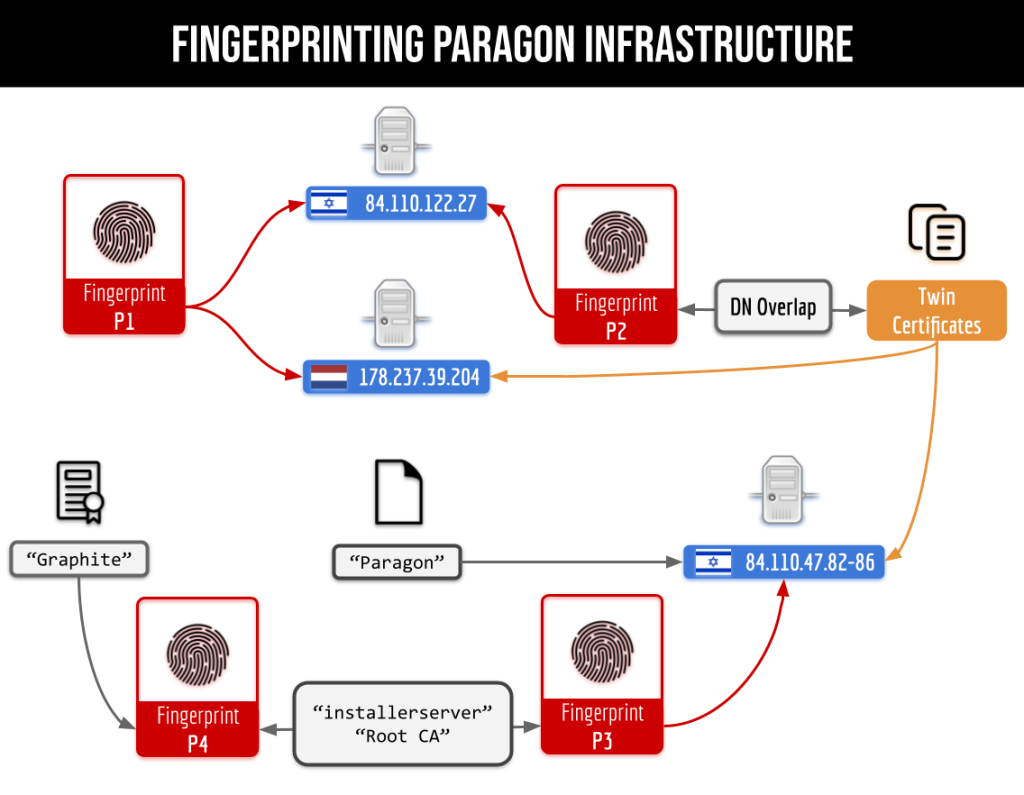
WhatsApp fixed zero-day flaw used to deploy Paragon Graphite spyware Pierluigi Paganini March 20, 2025 WhatsApp fixed a zero-click, zero-day…
Department of Homeland Security officials in charge of the Cybersecurity and Infrastructure Security Agency’s (CISA) Continuous Diagnostics and Mitigation (CDM)…
Kali Linux has released version 2025.1a, the first version of 2025, with one new tool, desktop changes, and a theme…
Moving Beyond Detection to Real-Time, Automated Security Across Workloads, Cloud, and Infrastructure SecPod, a global cybersecurity provider, has announced the…
Vocus has been cleared by the competition watchdog to buy TPG Telecom’s fixed-line business, transmission network and enterprise customer base…
A federal appeals court overruled a district court judge’s sentence for Capital One hacker Paige Thompson this week, deciding that…
A malware operation dubbed ‘DollyWay’ has been underway since 2016, compromising over 20,000 WordPress sites globally to redirect users to malicious sites….
A new Windows zero-day vulnerability is being actively exploited by at least 11 hacking groups linked to nation-states including North…
Sydney, Australia, March 19th, 2025, CyberNewsWire Sydney-based cybersecurity software company Knocknoc has raised a seed round from US-based venture capital…
The Department of Home Affairs is looking to adopt secure service edge (SSE) as part of efforts to modernise its…
Microsoft is investigating an ongoing outage preventing Outlook on the web users from accessing their Exchange Online mailboxes. According to…