In today’s digital world, data security and privacy are more critical than ever. With the increasing number of cyberattacks, data…
93% of organizations made policy changes over the preceding 12 months to address concerns about increased personal liability for CISOs,…
Adobe CIO Cynthia Stoddard chats with Computer Weekly at a hotel near Blackfriars Bridge in London and reflects on her…
Researchers have identified suspected government customers of spyware company Paragon Solutions in six more countries that hadn’t previously been publicly…
In a significant discovery, PRODAFT’s security research team has identified two critical vulnerabilities in the mySCADA myPRO Manager, a widely…
Europol has raised an urgent and serious alarm about the growing menace of hybrid cyber threats, particularly those orchestrated by…
Month by month, the number of ransomware attacks rose 50% from January 2025 to February, and just under 40% of…
California Cryobank, the largest US sperm bank, disclosed a data breach Pierluigi Paganini March 19, 2025 California Cryobank, the largest…
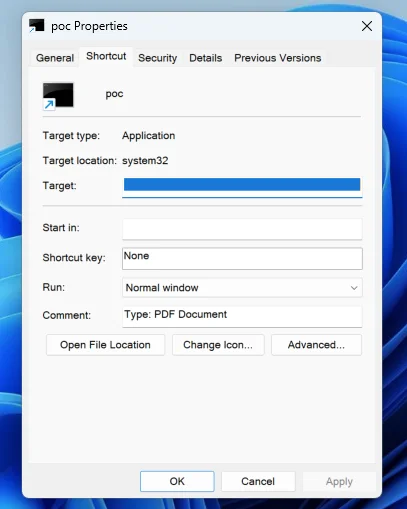
A newly identified cybersecurity threat involves attackers embedding malicious Word files within PDFs to deceive detection systems. This technique, confirmed…
Austin, TX, United States, March 19th, 2025, CyberNewsWire The average corporate user now has 146 stolen records linked to their…
State-sponsored threat actors and cybercrime groups from North Korea, Iran, Russia, and China have been exploiting a zero-day Windows vulnerability…
Most organizations today have invested in an email security solution of some description. But even the most premium tools have…