A sophisticated phishing campaign is targeting cryptocurrency investors with fraudulent emails claiming a mandatory Coinbase wallet migration requirement. These deceptive…
A critical vulnerability has been discovered in AMI’s MegaRAC software, which is used in Baseboard Management Controllers (BMCs) across various…
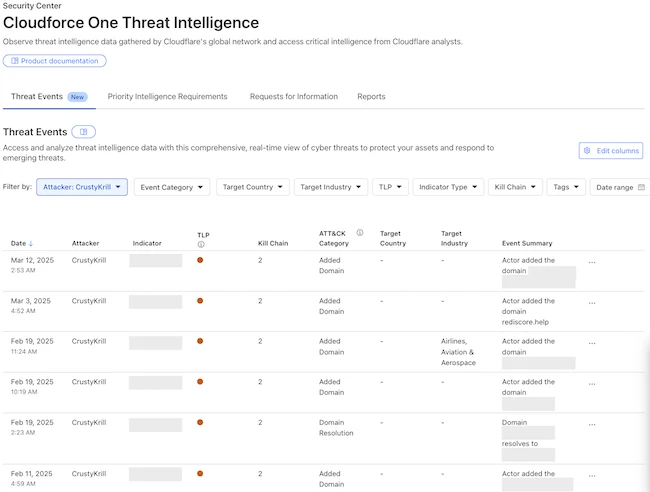
Cloudflare launched the Cloudforce One threat events platform to provide real-time intelligence on cyberattacks occurring across the Internet. Based on…
Most organizations are using AI in some way today, whether they know it or not. Some are merely beginning to…
A severe vulnerability in Synology’s DiskStation Manager (DSM) allows remote attackers to execute arbitrary code with no user interaction. The…
In a significant development, the China-aligned advanced persistent threat (APT) group known as MirrorFace has been observed employing sophisticated tactics…
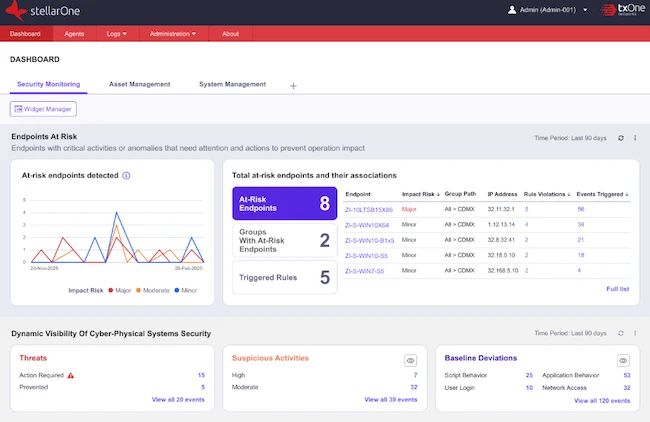
TXOne Networks announced Version 3.2 of its Stellar solution, further enhancing its capabilities from endpoint protection to more comprehensive detection…
A critical vulnerability in Windows File Explorer, identified as CVE-2025-24071, enables attackers to steal NTLM hashed passwords without any user…
The Cybersecurity and Infrastructure Security Agency (CISA) has sounded the alarm over a critical supply-chain attack affecting a widely used…
The New Zealand Computer Emergency Response Team (CERT NZ) has issued an urgent security advisory warning of a critical vulnerability,…
A sophisticated cyberattack has been uncovered, targeting booking websites to spread the LummaStealer malware. This campaign leverages fake CAPTCHA prompts…
Sydney, Australia, March 19th, 2025, CyberNewsWire Sydney-based cybersecurity software company Knocknoc has raised a seed round from US-based venture capital…