US sperm donor giant California Cryobank is warning customers it suffered a data breach that exposed customers’ personal information. California…
We were alerted to Mac and Windows stealers currently distributed via Reddit posts targeting users engaging in cryptocurrency trading. One…
SAP’s global CEO Christian Klein and chief operating officer Sebastian Steinhaeuser are in Australia this week, meeting customers and partners…
Google’s parent company, Alphabet, has announced its acquisition of Wiz, a leading cloud and cybersecurity platform for $32 billion. This…
Google’s $32bn (£24.6bn) acquisition of cloud native application protection platform (CNAPP) provider Wiz has been hailed as both the world’s…
The Australian National University has a new chief information security officer, with Julian Doak joining from the Australian Bureau of Statistics….
Nvidia CEO Jensen Huang said the company was well placed to navigate a shift in the artificial intelligence industry, in…
Cybercriminals used information-stealing malware to a devastating effect last year, capturing sensitive data that fueled ransomware, breaches and attacks targeting…
Arizona-based Western Alliance Bank is notifying nearly 22,000 customers their personal information was stolen in October after a third-party vendor’s…
China has accused four Taiwanese individuals of being hackers associated with Taiwan’s military cyber force, claiming they were responsible for…
Facebook and Instagram-owner Meta Platforms said its independent fact-checking program in Australia would help detect and remove false content and…
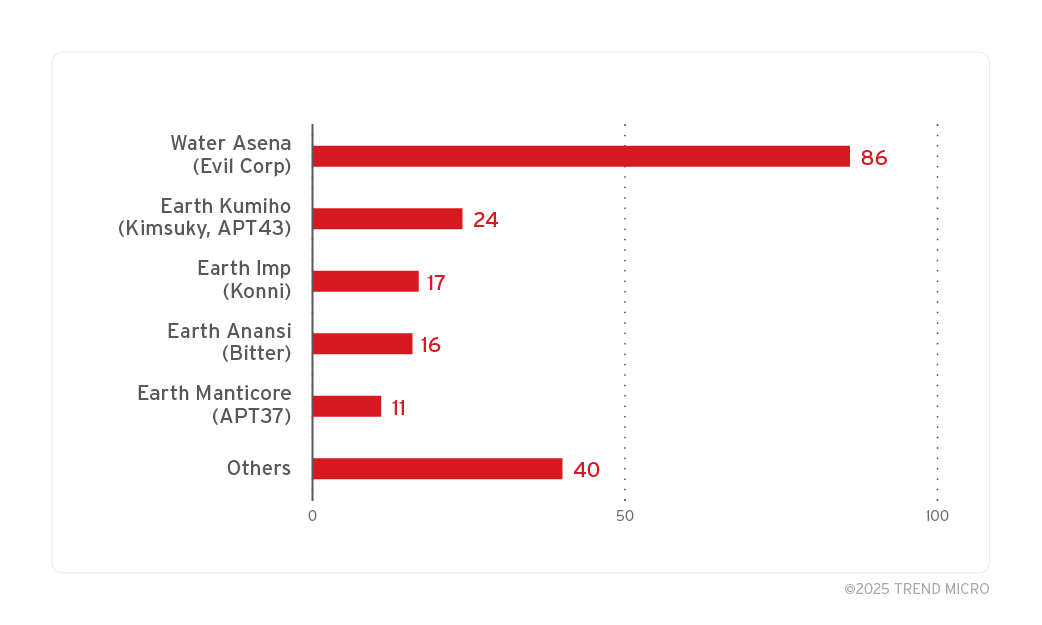
Nation-state actors and cybercrime gangs abuse malicious .lnk files for espionage and data theft Pierluigi Paganini March 18, 2025 11…