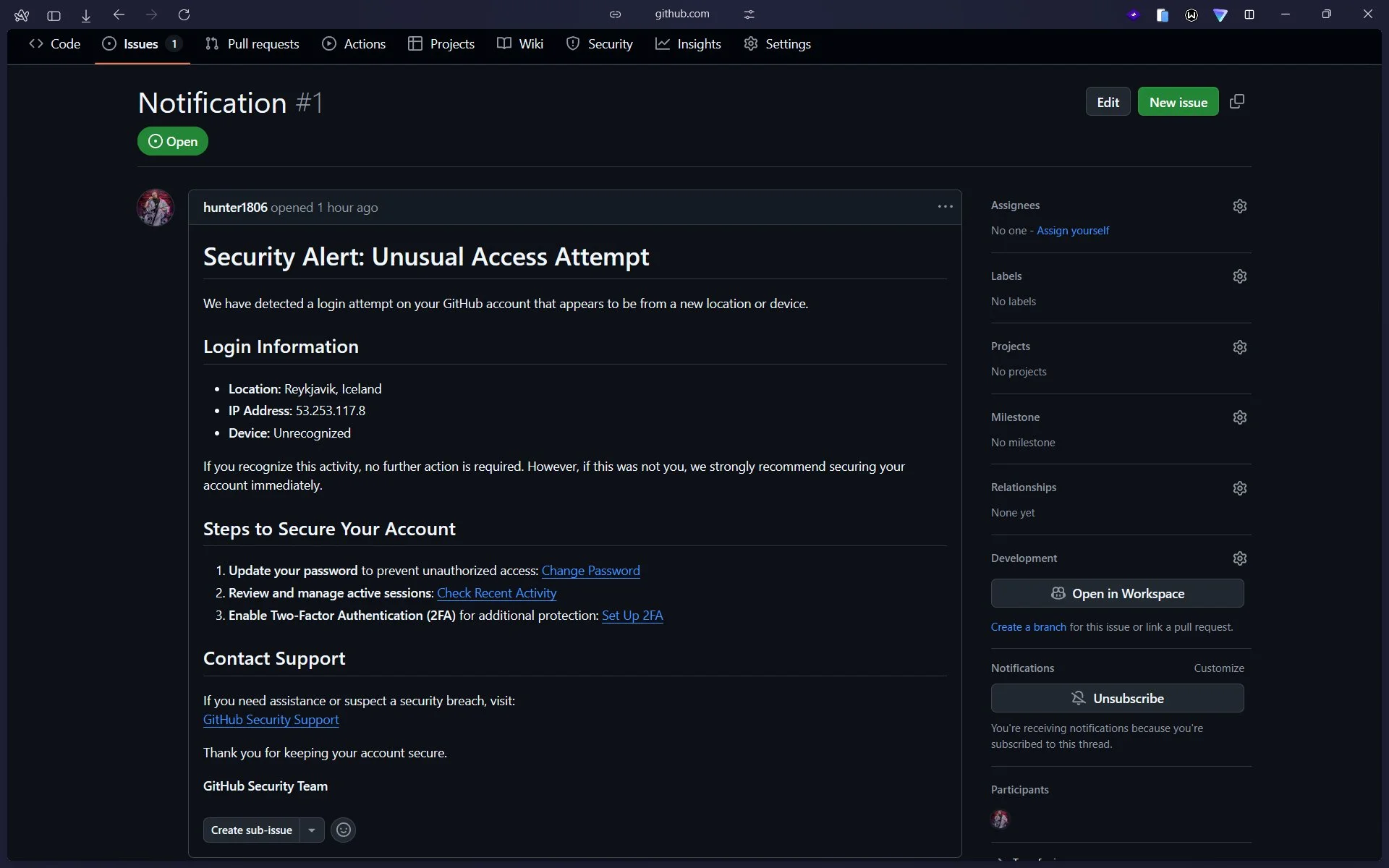
A phishing campaign targeting GitHub account owners has been trying to scare them with a fake security alert into allowing…
Mar 17, 2025Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers are calling attention to an incident in which the popular GitHub…
Researcher releases free GPU-Based decryptor for Linux Akira ransomware Pierluigi Paganini March 17, 2025 A researcher released a free decryptor…
Apple has announced the integration of end-to-end encryption (E2EE) for Rich Communication Services (RCS) on iPhones. This development follows the…
Frankfurt am Main, Germany, March 17th, 2025, CyberNewsWire Cyberattacks are no longer an abstract threat – they dominate risk planning…
Frankfurt am Main, Germany, March 17th, 2025, CyberNewsWire Cyberattacks are no longer an abstract threat – they dominate risk planning…
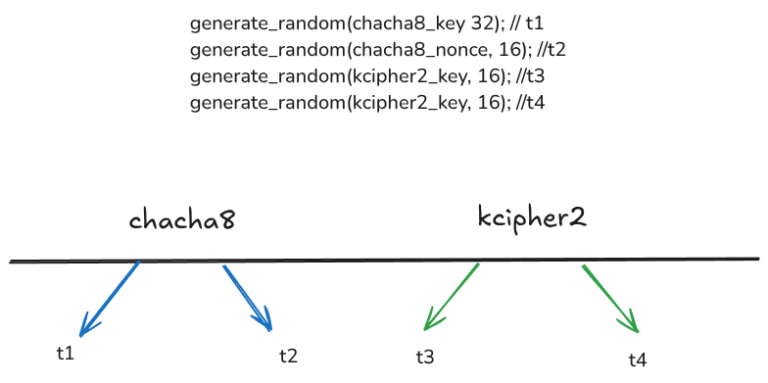
The Indian – Computer Emergency Response Team (CERT-In) issued a critical vulnerability note, CIVN-2025-0048, detailing several vulnerabilities in the Rising…
Researcher releases free GPU-Based decryptor for Linux Akira ransomware Pierluigi Paganini March 17, 2025 A researcher released a free decryptor…
If you’ve driven a car, used cloud services or even turned on a smart faucet, you’ve likely benefited from the…
A recent and significant cybersecurity threat has emerged involving a critical vulnerability in Apache Tomcat, identified as CVE-2025-24813. This vulnerability…
Cybersecurity experts have uncovered how hackers use Cascading Style Sheets (CSS) to deceive spam filters and monitor user behavior. This…
March 14, 2025 – A shocking amount of iOS apps in Apple’s App Store contained hard-coded secrets. Secrets that could…