Most microsegmentation projects fail before they even get off the ground—too complex, too slow, too disruptive. But Andelyn Biosciences proved…
Over 80% of global companies are now using AI to improve business operations. AI has also become a feature of…
Two critical authentication bypass vulnerabilities have been discovered in the ruby-saml library, potentially exposing numerous web applications to account takeover…
A recent alert from the Akamai Security Intelligence and Response Team (SIRT) has highlighted the exploitation of a severe command…
Mar 14, 2025The Hacker NewsData Protection / Ransomware Cyber threats evolve daily. In this live webinar, learn exactly how ransomware…
A cloud market characterised by openness, interoperability, and fairness has to be the aspiration for Europe, but we are currently…
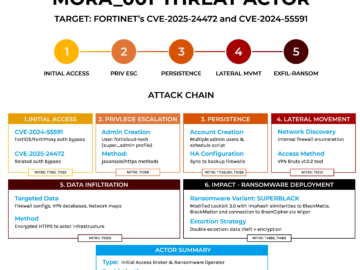
SuperBlack Ransomware operators exploit Fortinet Firewall flaws in recent attacks Pierluigi Paganini March 14, 2025 Operators behind the SuperBlack ransomware…
Cisco has issued security advisories for multiple vulnerabilities affecting its IOS XR Software, with particular emphasis on a significant memory…
A critical security vulnerability has been identified in the ruby-saml library, a popular tool used for Single Sign-On (SSO) via…
Researchers have identified a series of sophisticated attacks by the notorious Lazarus group targeting South Korean web servers. The threat…
Over the past decade, encrypted communication has become the norm for billions of people. Every day, Signal, iMessage, and WhatsApp…
The notorious Lazarus group has been identified as leveraging compromised IIS servers to deploy malicious ASP web shells. These sophisticated…