Cary, North Carolina, March 13th, 2025, CyberNewsWire As Artificial Intelligence (AI)-powered cyber threats surge, INE Security, a global leader in…
The departures have strained a workforce that was already stretched thin. “We were running into [a] critical skills shortage previously,”…
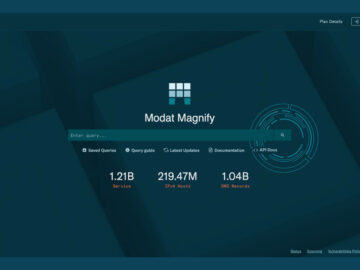
The Hague, the Netherlands, March 13th, 2025, CyberNewsWire Founded in 2024, Modat – the European-crafted, research-driven, AI-powered cybersecurity company, has…
Mar 13, 2025Ravie LakshmananBrowser Security / Encryption Browser maker Mozilla is urging users to update their Firefox instances to the…
Medusa ransomware hit over 300 critical infrastructure organizations until February 2025 Pierluigi Paganini March 13, 2025 The Medusa ransomware operation…
Amelia Coen | 13 March 2025 at 08:49 UTC Security is a team sport. Whether you’re a pentester, bug bounty…
Click here for full interview. In this show, we speak with Tanya Janca, aka SheHacksPurple, a renowned code security trainer…
Mar 13, 2025Ravie LakshmananOpen Source / Vulnerability Meta has warned that a security vulnerability impacting the FreeType open-source font rendering…
A vulnerability has been discovered in the Tenda AC7 router, firmware version V15.03.06.44, which allows attackers to execute malicious payloads…
Cupertino, California – March 13, 2025 – Cyble, a leading global cybersecurity and threat intelligence provider, is proud to announce…
Cybersecurity researchers have uncovered a sophisticated cyber espionage campaign targeting critical network infrastructure, marking a significant evolution in tactics by…
For business leaders around the globe, AI promises an exciting edge in innovation and efficiency. The rapid evolution of AI…