In recent years, T-Mobile has faced a series of high-profile data breaches that have raised concerns about the security of…
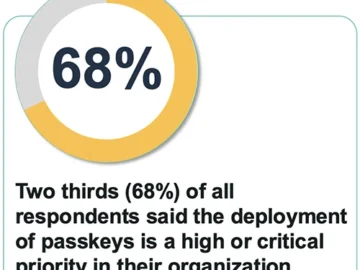
87% of companies have, or are in the midst of, rolling out passkeys with goals tied to improved user experience,…
Apple has patched a vulnerability in iPhone and iPad that was under active exploitation by cybercriminals. The update is available…
The Competition and Markets Authority’s (CMA) final report into the mobile browser market has found innovation is being held back…
Sean Plankey has been nominated to be the next director of the U.S. Cybersecurity and Infrastructure Security Agency (CISA). Plankey…
Slovak cybersecurity company ESET says a newly patched zero-day vulnerability in the Windows Win32 Kernel Subsystem has been exploited in…
Technologies such as Low-Code/No-Code (LCNC) and Robotic Process Automation (RPA) have become fundamental in the digital transformation of companies. They continue to…
CYREBRO, the AI-native Managed Detection and Response (MDR) solution, announced today that it won Silver in the category of Security…
Mar 12, 2025Ravie LakshmananCyber Espionage / Vulnerability The China-nexus cyber espionage group tracked as UNC3886 has been observed targeting end-of-life…
Mozilla is warning Firefox users to update their browsers to the latest version to avoid facing disruption and security risks…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory regarding a significant vulnerability in the Microsoft Windows…
Sports betting is a multi-billion-dollar industry, but behind the flashing lights and promises of easy money lies a hidden underworld…